mirror of https://github.com/D4-project/d4-core
|
|
||
|---|---|---|
| .. | ||
| analyzer | ||
| configs | ||
| documentation | ||
| gen_cert | ||
| lib | ||
| update | ||
| web | ||
| workers | ||
| .gitignore | ||
| Dockerfile.analyzer-d4-passivedns | ||
| Dockerfile.d4-server | ||
| LAUNCH.sh | ||
| README.md | ||
| docker-compose.yml | ||
| install_server.sh | ||
| requirement.txt | ||
| sensors_manager.py | ||
| server.py | ||
README.md
D4 core
D4 core server
D4 core server is a complete server to handle clients (sensors) including the decapsulation of the D4 protocol, control of sensor registrations, management of decoding protocols and dispatching to adequate decoders/analysers.
Requirements
- Python 3.6
- GNU/Linux distribution
Installation
Install D4 server
cd server
./install_server.sh
Create or add a pem in d4-core/server :
cd gen_cert
./gen_root.sh
./gen_cert.sh
cd ..
Launch D4 server
./LAUNCH.sh -l
The web interface is accessible via http://127.0.0.1:7000/
Updating web assets
To update javascript libs run:
cd web
./update_web.sh
API
Notes
- All server logs are located in
d4-core/server/logs/ - Close D4 Server:
./LAUNCH.sh -k
D4 core server
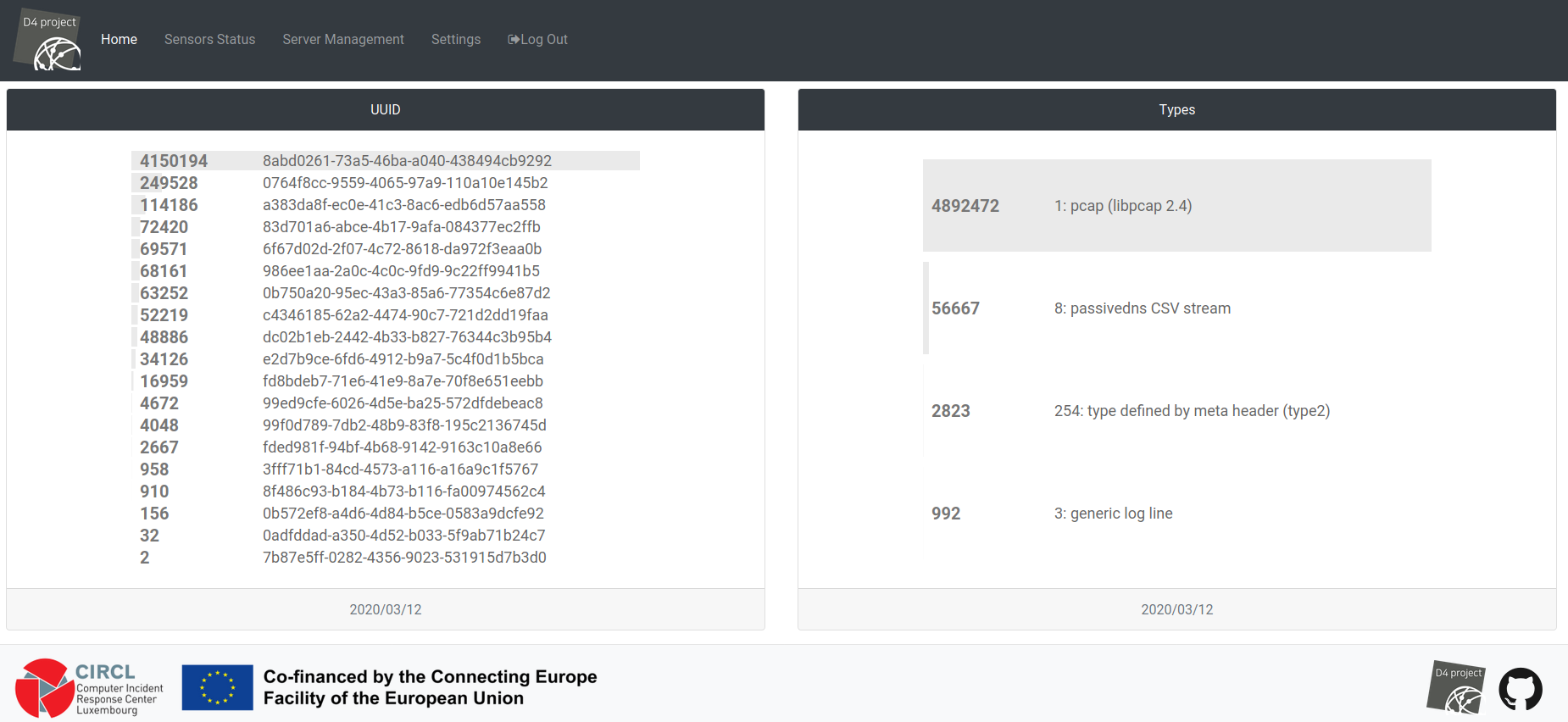
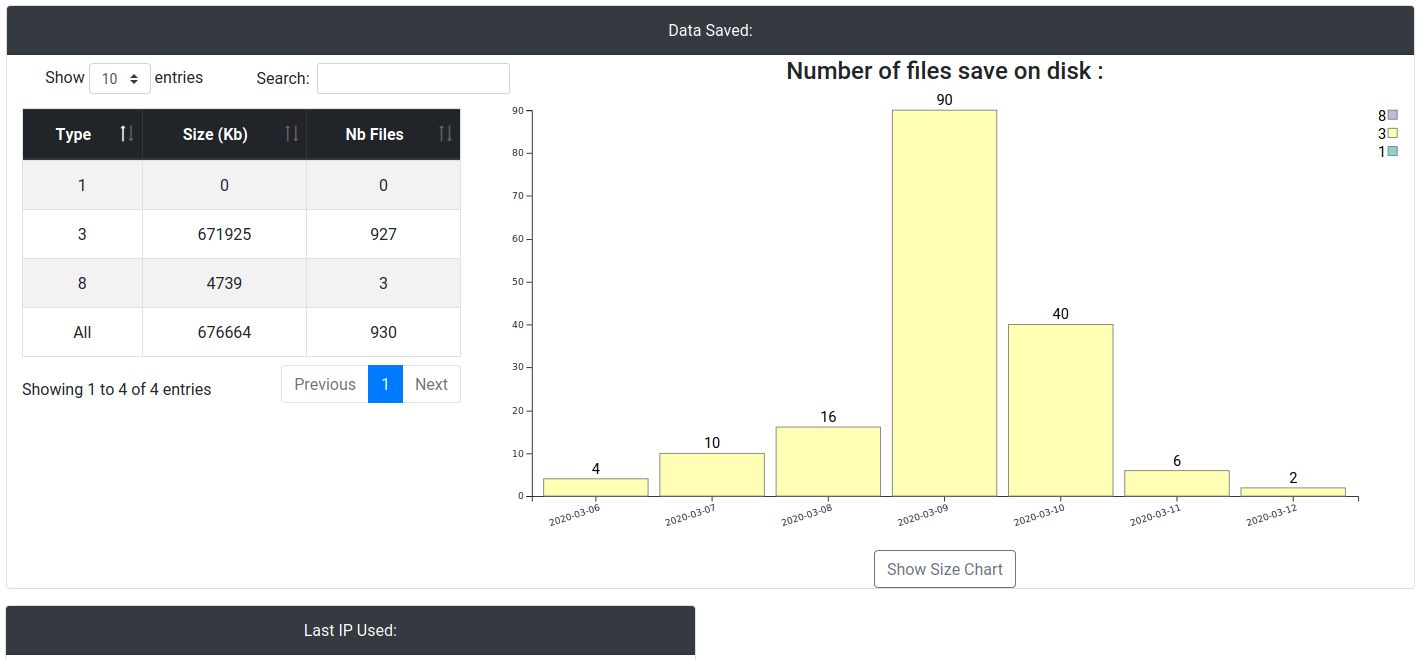
Dashboard:
Connected Sensors:
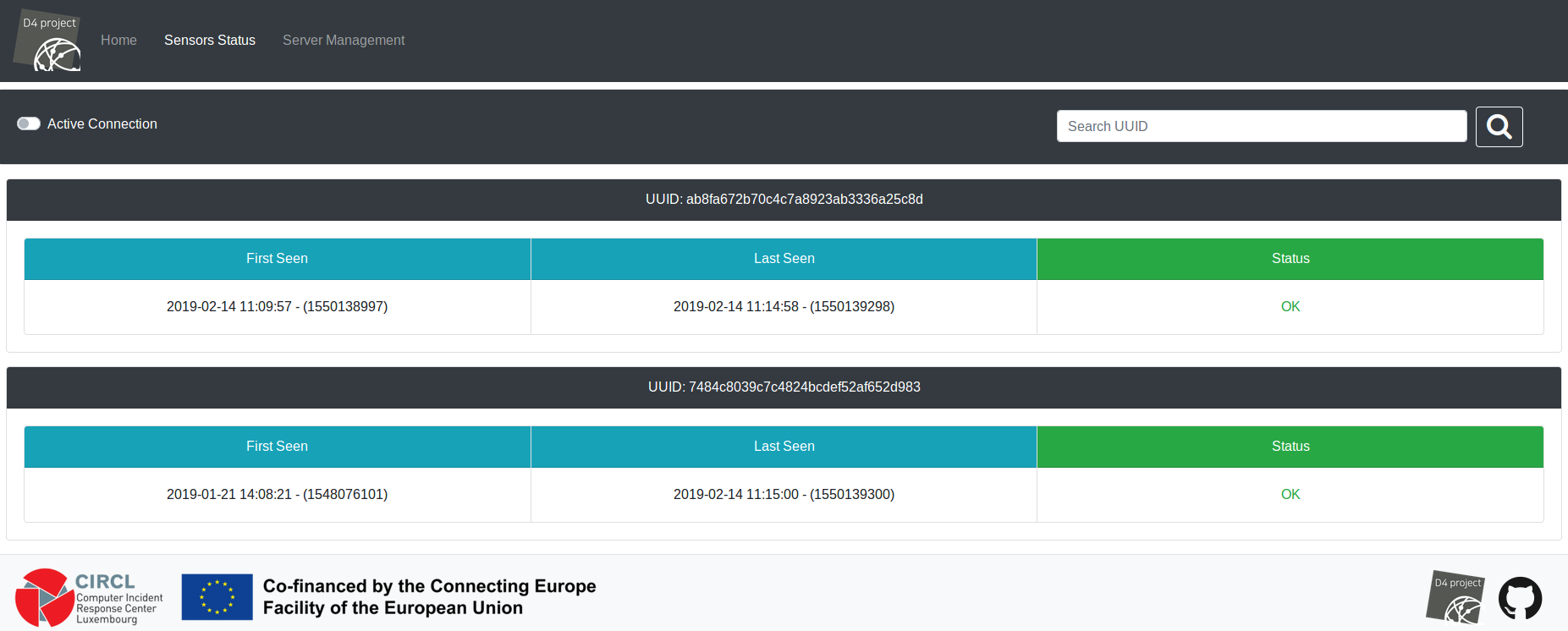
Sensors Status:
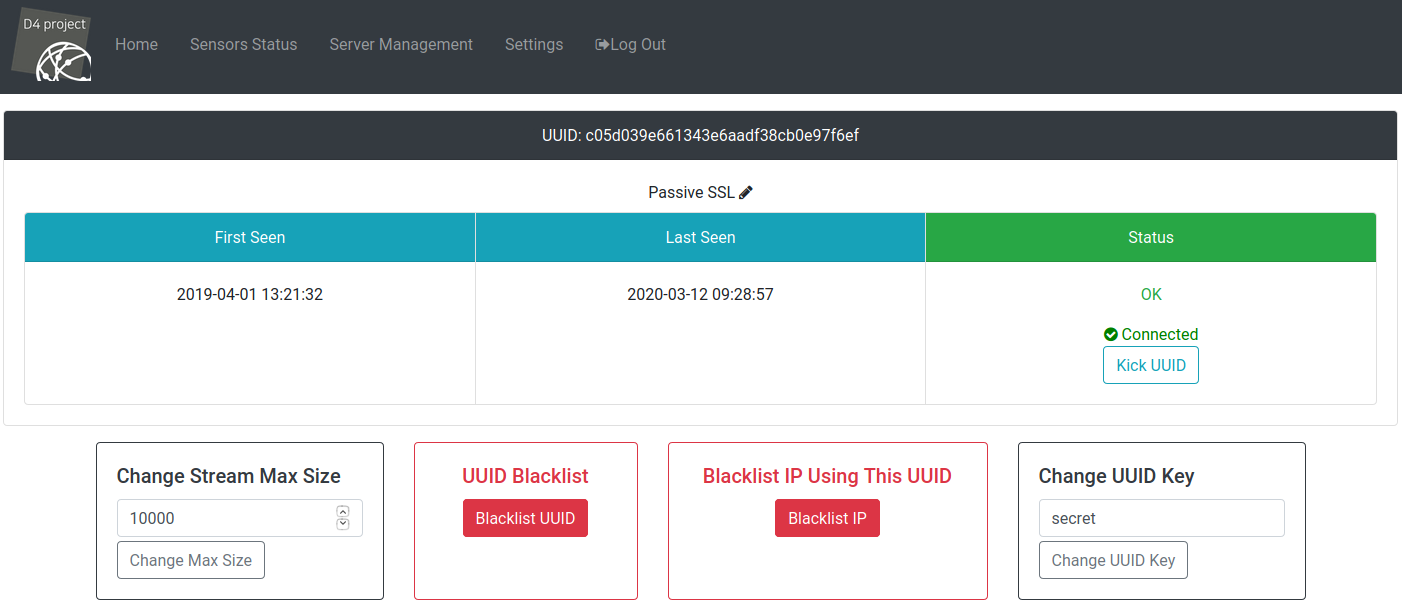
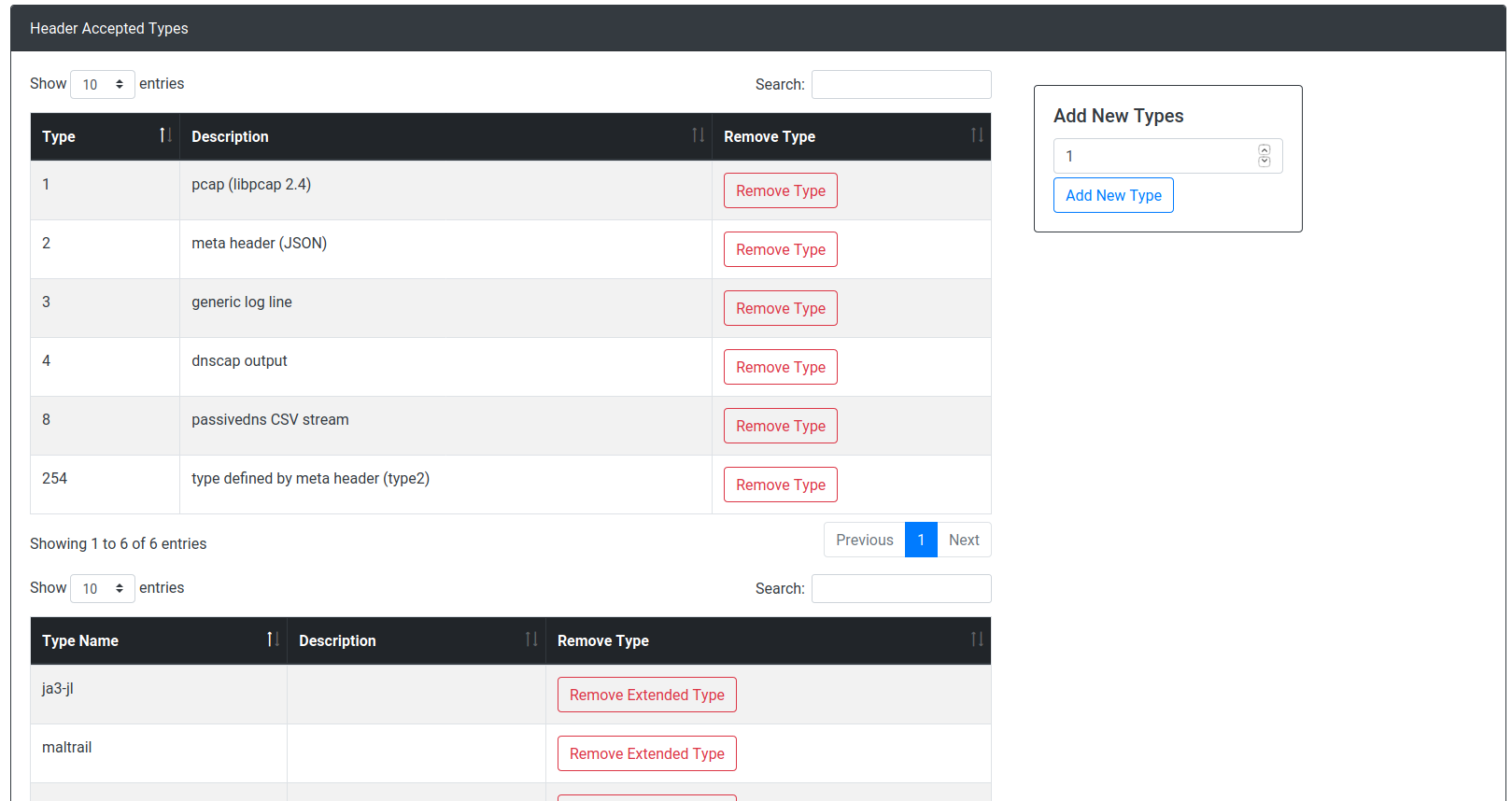
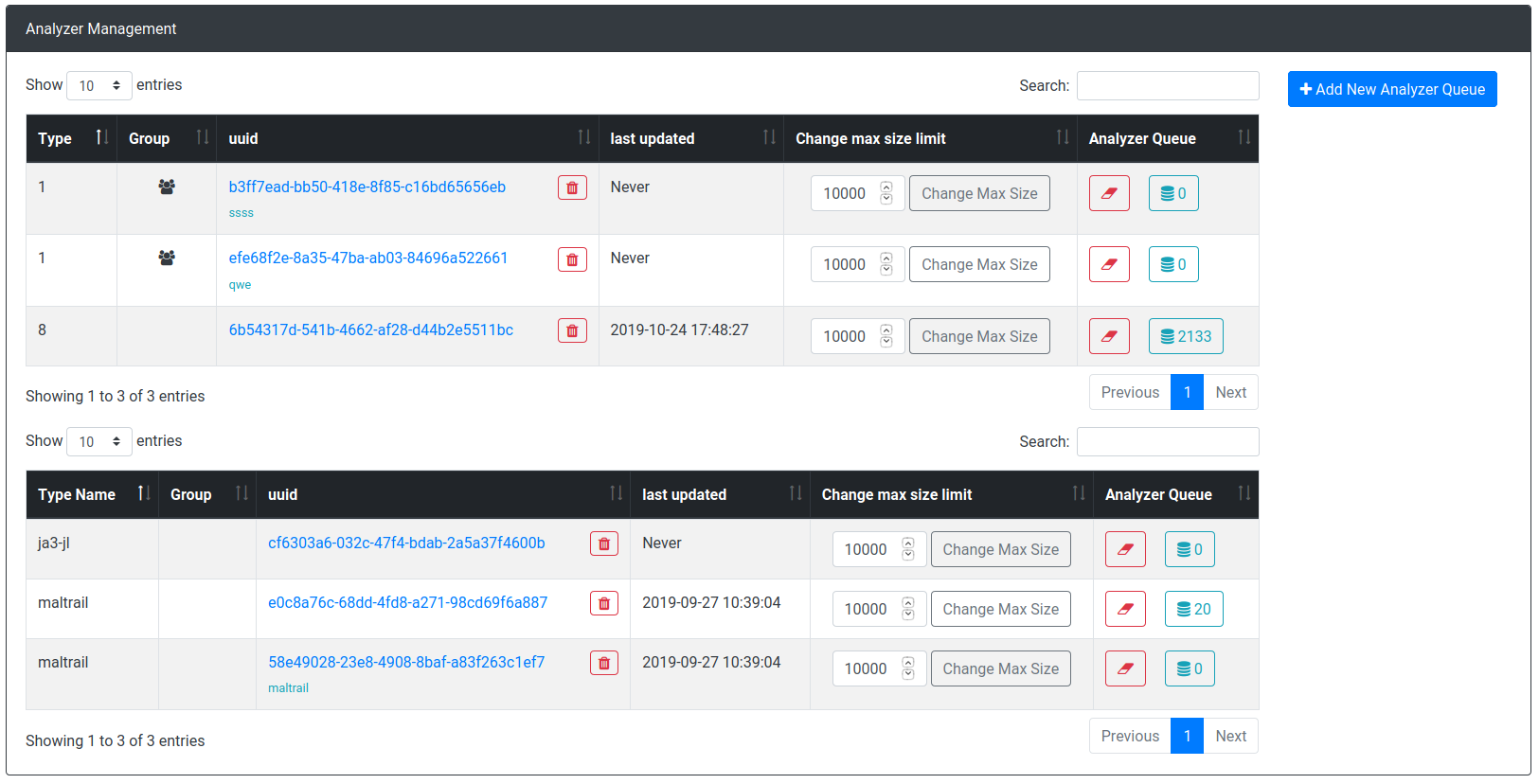
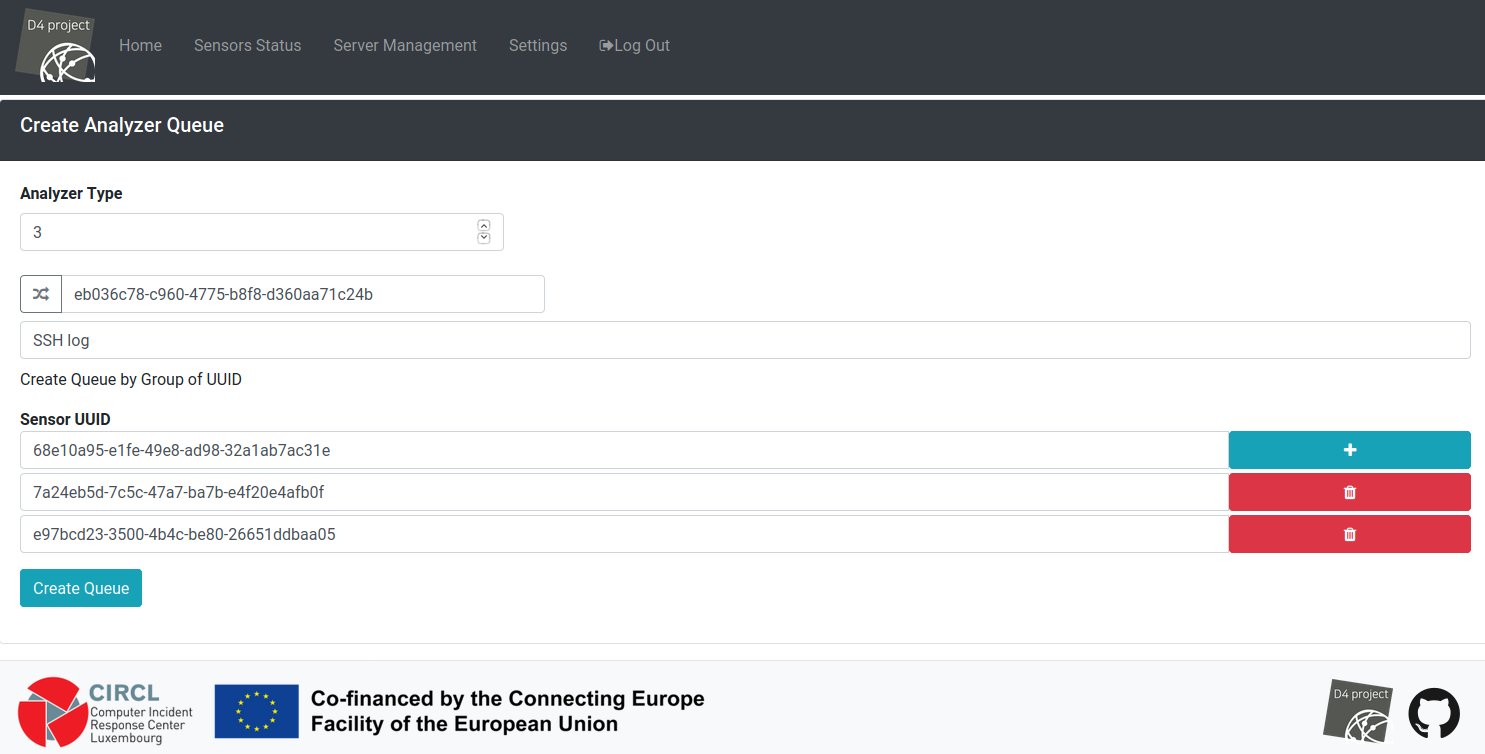
Server Management:
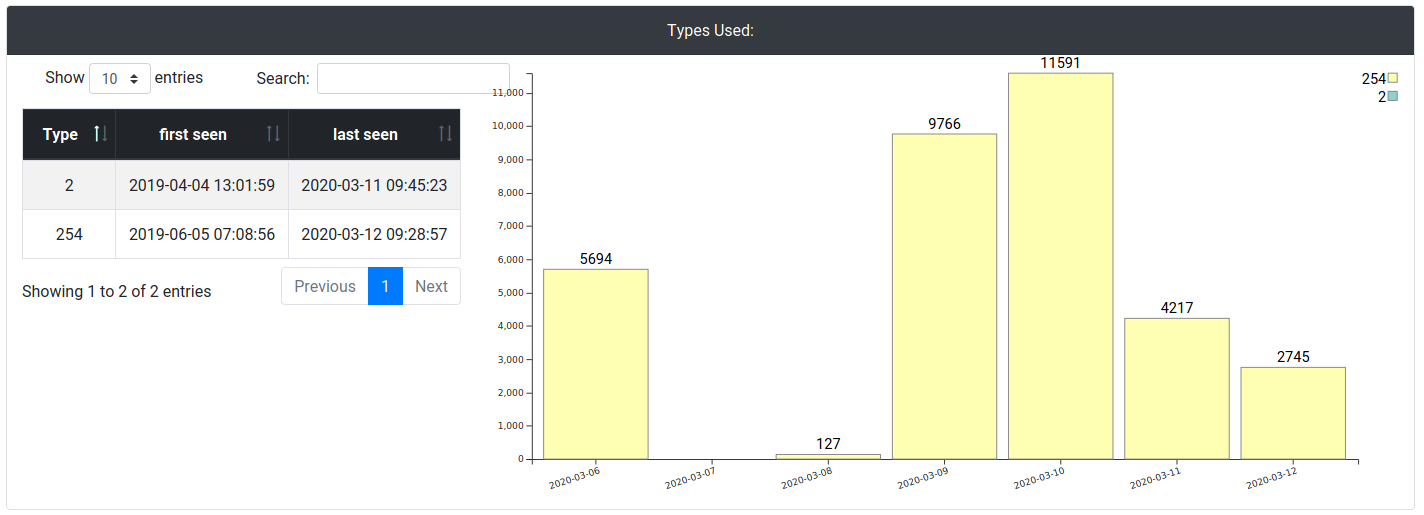
analyzer Queues:
Troubleshooting
Worker 1, tcpdump: Permission denied
Could be related to AppArmor:
sudo cat /var/log/syslog | grep denied
Run the following command as root:
aa-complain /usr/sbin/tcpdump