Fixing broken link |
||
|---|---|---|
| .. | ||
| figures | ||
| README.md | ||
README.md
Galaxies
Galaxies in MISP are a method used to express a large object called cluster that can be attached to MISP events or attributes. A cluster can be composed of one or more elements. Elements are expressed as key-values.
There are default vocabularies available in MISP galaxy but those can be overwritten, replaced or updated as you wish. Vocabularies are from existing standards (like STIX, Veris, MISP and so on) or custom ones.
Existing clusters and vocabularies can be used as-is or as a template. MISP distribution can be applied to each cluster to permit a limited or broader distribution scheme.
The objective is to have a common set of clusters for organizations starting analysis but that can be expanded to localized information (which is not shared) or additional information (that can be shared).
MISP galaxy are available on Github.
Managing Galaxies in MISP
[warning] You need to have a specific role to manage Galaxies on a MISP instance.
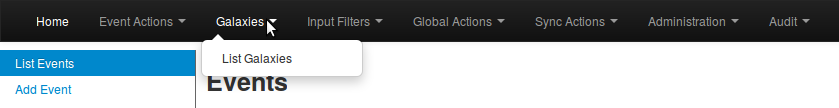
Galaxies management is accessed using the Galaxies link on the top menu.
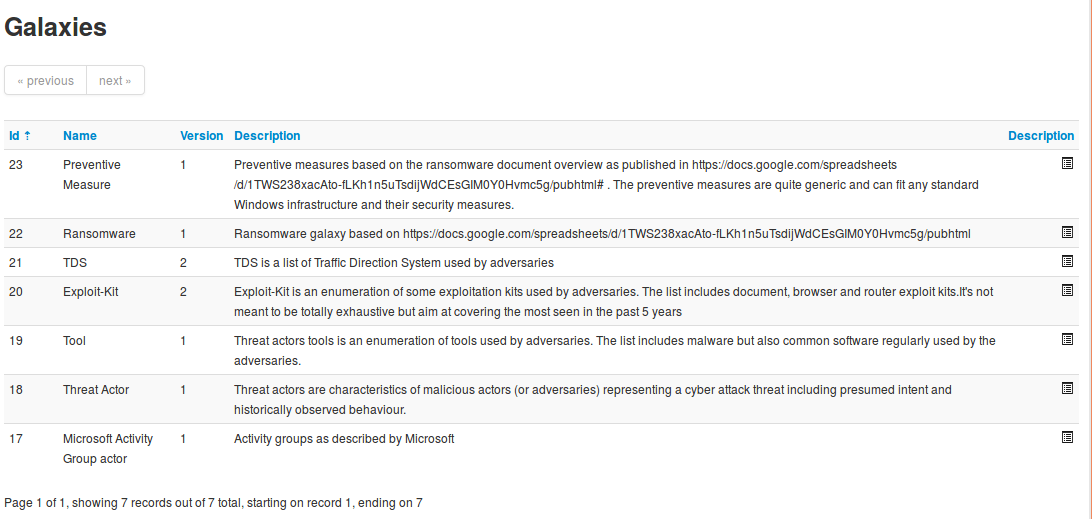
A list with all the galaxies existing on the server will appear.
Each galaxy can be explored using the icon at the end of the line.
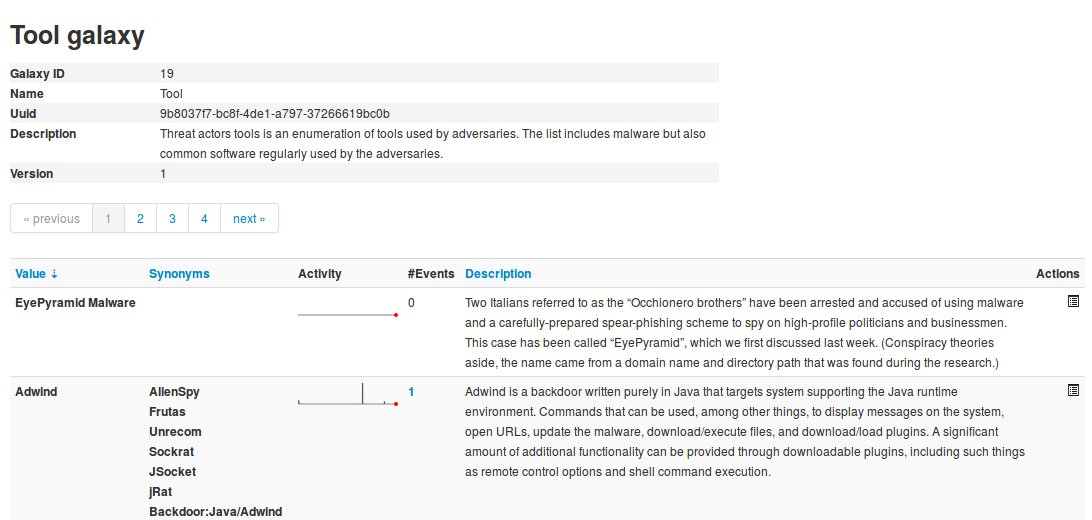
Here is shown the metadata of the selected galaxy as well as a table with each available value as well as some complementary data such as a description of the value or the activity, that is to say the evolution of the use of each value.
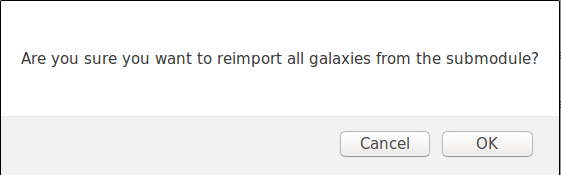
Galaxies can be reimported from the submodules by cliking the "Update Galaxies" link on either the galaxies list or while browsing a specific galaxy. A popup will appear to confirm the reimportation.
All galaxies will always be updated, even while browsing a specific galaxy.
Using Galaxies in MISP Events - Example
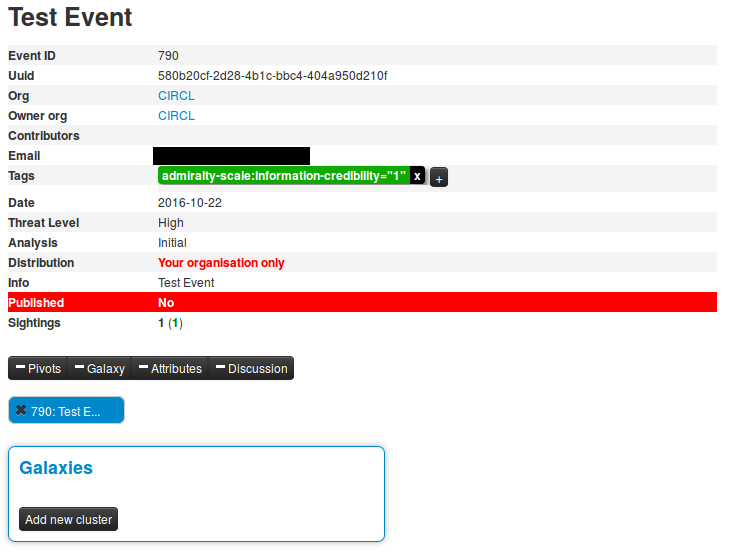
For this example, we will try to add a cluster to an existing event. This cluster will contains informations about threat actor known as Sneaky Panda.
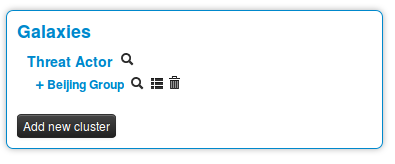
Here on the event view, we notice a blue frame under the metadatas with the title "Galaxies" and a button "Add new cluster". Let's click on the latter to begin.
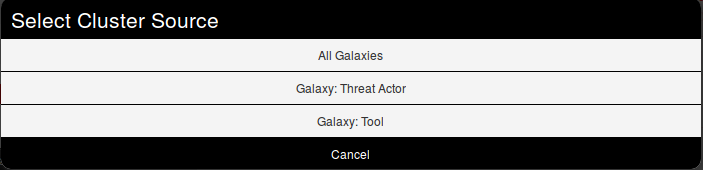
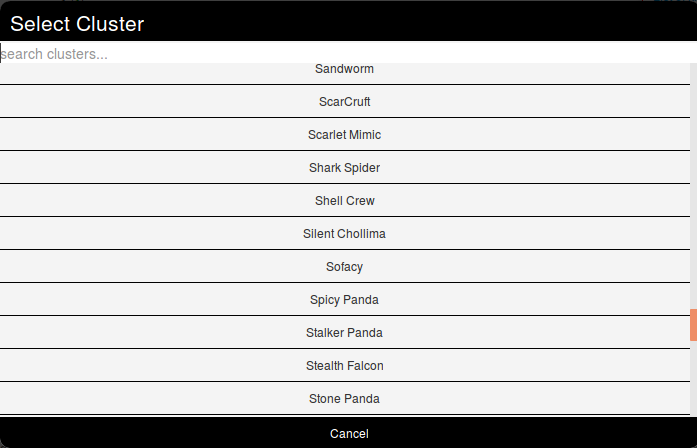
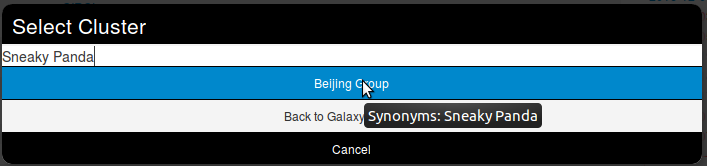
A popup will appear proposising to explore a particular galaxy or all at the same time. Here, as we know we want to as a threat actor, we will choose the second option and scroll to find Sneaky Panda (We are courageous, aren't we?).
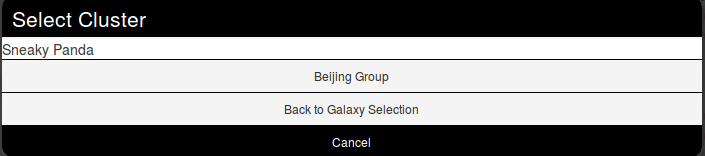
Wait. No Sneaky Panda? Hm that's strange. Or maybe it is only registred as a alias. Let's have a look! To do so we will use the search field which stay on top of the list. So what do we get? Beijing Group, is it an alias of our threat actor.
Pointing the cursor on it will give us the answer.
We have a match. So we select it and here we go.
Clicking on the magnifying glass next to Threat actor redirects to the list of all threat actors Clicking on the magnifying glass next to Beijing Group redirects us to a page about this group Clicking on the addition symbole on the left of Beijing Group extends the module.
Available Galaxies
Clusters
Android - Android malware galaxy based on multiple open sources.
Banker - A list of banker malware.
Exploit Kit - Exploit-Kit is an enumeration of some exploitation kits used by adversaries. The list includes document, browser and router exploit kits. It's not meant to be totally exhaustive but aim at covering the most seen in the past 5 years.
Microsoft Activity Group - Activity groups as described by Microsoft.
Preventive Measure - Preventive measures.
Ransomware - Ransomware galaxy based on https://docs.google.com/spreadsheets/d/1TWS238xacAto-fLKh1n5uTsdijWdCEsGIM0Y0Hvmc5g/pubhtml
RAT - remote administration tool or remote access tool (RAT), also called sometimes remote access trojan, is a piece of software or programming that allows a remote "operator" to control a system as if they have physical access to that system.
TDS - TDS is a list of Traffic Direction System used by adversaries.
Threat Actor - Adversary groups - Known or estimated adversary groups targeting organizations and employees. Adversary groups are regularly confused with their initial operation or campaign. MISP
Tool - tool is an enumeration of tools used by adversaries. The list includes malware but also common software regularly used by the adversaries.
MITRE Attack Pattern - Attack Pattern - MITRE Adversarial Tactics, Techniques & Common Knowledge (ATT&CK)
MITRE Course of Action - Course of Action - MITRE Adversarial Tactics, Techniques & Common Knowledge (ATT&CK)
MITRE Intrusion Set - Intrusion Test - MITRE Adversarial Tactics, Techniques & Common Knowledge (ATT&CK)
MITRE Malware - Malware - MITRE Adversarial Tactics, Techniques & Common Knowledge (ATT&CK)
MITRE Tool - Tool - MITRE Adversarial Tactics, Techniques & Common Knowledge (ATT&CK)
Sectors - Activity sectors
CertEU Govsector - Cert EU GovSector/master/clusters/tool.json) - Enumeration of software tools used by adversaries. The list includes malware but also common software regularly used by the adversaries.
Vocabularies
Common
certainty-level - Certainty level of an associated element or cluster.
threat-actor-type - threat actor type vocab as defined by Cert EU.
ttp-category - ttp category vocab as defined by Cert EU.
ttp-type - ttp type vocab as defined by Cert EU.
threat-actor
cert-eu-motive - Motive vocab as defined by Cert EU.
intended-effect-vocabulary - The IntendedEffectVocab is the default STIX vocabulary for expressing the intended effect of a threat actor. STIX 1.2.1
motivation-vocabulary - The MotivationVocab is the default STIX vocabulary for expressing the motivation of a threat actor. STIX 1.2.1
planning-and-operational-support-vocabulary - The PlanningAndOperationalSupportVocab is the default STIX vocabulary for expressing the planning and operational support functions available to a threat actor.
sophistication - The ThreatActorSophisticationVocab enumeration is used to define the default STIX vocabulary for expressing the subjective level of sophistication of a threat actor.
type - The ThreatActorTypeVocab enumeration is used to define the default STIX vocabulary for expressing the subjective type of a threat actor