mirror of https://github.com/MISP/misp-website
chg: [blog] migration of news pages
parent
2c7eff4a56
commit
94d733a9f4
|
|
@ -1,6 +1,7 @@
|
|||
---
|
||||
title: MISP 2.4.49 released with many improvements and fixes
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
date: 2016-07-22
|
||||
layout: post
|
||||
---
|
||||
|
||||
|
|
@ -1,6 +1,7 @@
|
|||
---
|
||||
title: MISP Hackathon 2016
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
date: 2016-08-01
|
||||
layout: post
|
||||
---
|
||||
|
||||
|
|
@ -1,6 +1,7 @@
|
|||
---
|
||||
title: MISP 2.4.50 released including new features, security and bug fixes.
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
date: 2016-08-10
|
||||
layout: post
|
||||
---
|
||||
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP training, “the Brussels Edition”, CIRCL in collaboration with CERT.EU - September 5th 2016
|
||||
date: 2016-08-11
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
On September 5th 2016 and after 3 successful editions, the MISP (Malware Information and Threat Sharing Platform) training is traveling to Brussels. This workshop is organized by [CIRCL](https://www.circl.lu/) in collaboration with [CERT-EU](https://cert.europa.eu) and will take place at the European Economic and Social Committee’s premises.
|
||||
|
|
@ -1,6 +1,7 @@
|
|||
---
|
||||
title: Building an OCR import module in MISP
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
date: 2016-08-12
|
||||
layout: post
|
||||
---
|
||||
|
||||
|
|
@ -79,9 +80,9 @@ The module is automatically integrated in MISP via the [misp-modules framework](
|
|||
|
||||
An analyst will have access to the following MISP user-interfaces while using the OCR module. The module just work like an expansion module and the user will see all the potential indicators scanned from the document. The OCR module is included as an example in the misp-modules framework and can be directly enabled in the MISP configuration. In order to use the module, the [Tesseract OCR](http://miphol.com/muse/2013/05/install-tesseract-ocr-on-ubunt.html) have to be installed locally on your MISP instance.
|
||||
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
|
||||
|
|
@ -1,6 +1,7 @@
|
|||
---
|
||||
title: MISP 2.4.51 released including new features and many bug fixes.
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
date: 2016-08-29
|
||||
layout: post
|
||||
---
|
||||
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP Upcoming Activities in October and November 2016
|
||||
date: 2016-10-02
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
The next months for the MISP core team, it is full of interesting activities and upcoming events.
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.52 released including new features and major improvements
|
||||
date: 2016-10-07
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
We are glad to announce MISP 2.4.52 including new features, improvements and bug fixes.
|
||||
|
|
@ -10,7 +11,7 @@ The following new features were introduced:
|
|||
|
||||
- Freetext feed import: a flexible scheme to import any feed available on Internet and incorporate them automatically in MISP. The feed imported can create new event or update an existing event. The freetext feed feature permits to preview the import and quickly integrates external sources.
|
||||
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
|
||||
- [Bro NIDS](https://www.bro.org/) export added in MISP in addition to Snort and Suricata.
|
||||
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP Internet Drafts Published
|
||||
date: 2016-10-21
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
We recently released two Internet-Drafts describing the MISP format:
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.53 released
|
||||
date: 2016-10-22
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version [2.4.53](https://github.com/MISP/MISP/tree/v2.4.53) of MISP including several security fixes has been released.
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.54 released
|
||||
date: 2016-11-04
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version [2.4.54](https://github.com/MISP/MISP/tree/v2.4.54) of MISP including new features, bug and security fixes.
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: Independence and Threat Intelligence Platforms
|
||||
date: 2016-11-16
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
After the recent news of a [Threat Intelligence Platform vendor stopping its activities](http://soltra.com/en/articles/soltra-wind-down/), we have received some questions about our strategies as a Threat Intelligence Platform.
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.55 released
|
||||
date: 2016-11-22
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.55](https://github.com/MISP/MISP/tree/v2.4.55) has just been released, including bug fixes and improvements.
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.56 released
|
||||
date: 2016-12-07
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.56](https://github.com/MISP/MISP/tree/v2.4.56) has been released, including bug fixes and improvements.
|
||||
|
|
@ -10,8 +11,8 @@ This is the first version introducing the [misp-galaxy](https://github.com/MISP/
|
|||
large objects called cluster that can be attached to MISP events or (in the near future) attributes. A cluster can be composed of one or more elements,
|
||||
which are expressed as key-value pairs. You can now directly benefit from the shared galaxy with threat actors and tools used by attackers in MISP.
|
||||
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
|
||||
The release includes various improvements such as:
|
||||
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.57 released
|
||||
date: 2016-12-19
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.57](https://github.com/MISP/MISP/tree/v2.4.57) has been released, including bug fixes and improvements.
|
||||
|
|
@ -1,12 +1,13 @@
|
|||
---
|
||||
title: MISP 2.4.58 released
|
||||
date: 2016-12-22
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.58](https://github.com/MISP/MISP/tree/v2.4.58) has been released, including bug fixes and a specific improvement to the correlation feature.
|
||||
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
|
||||
Correlation can be disabled at the instance level, or, if a new setting is enabled, at the event or at the attribute level by a site admin or the creator of the event. The latter is an optional feature that can be enabled or disabled system-wide in MISP. This allows for a flexible scheme, supporting situations where the correlations of certain events or attributes are not interesting for the analysts. This feature is also available via the API.
|
||||
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: Information Sharing Maturity Model
|
||||
date: 2017-01-16
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
Here at the *MISP project*, we are practical oriented people. We create software (from *MISP core* to *MISP workbench*), develop data models (such as [taxonomies](https://github.com/MISP/misp-taxonomies), [warning-lists](https://github.com/MISP/misp-warninglists) and [galaxies](https://github.com/MISP/misp-galaxy)) and build practical standards to solve information sharing challenges and improve the general state of information sharing. That's what we strive for. If we lack something, we build it. If we see a requirement, we fullfil it.
|
||||
|
|
@ -1,12 +1,13 @@
|
|||
---
|
||||
title: MISP 2.4.60 released
|
||||
date: 2017-01-17
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.60](https://github.com/MISP/MISP/tree/v2.4.60) has been released, including bug fixes and the long awaited attribute-level tagging feature.
|
||||
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
|
||||
All tags (local or from taxonomies) can now be also applied at the attribute level. This allows analysts or users to easily classify attributes
|
||||
within an event. Many of the taxonomies have useful properties that can be applied to provide additional contextual information to attributes.
|
||||
|
|
@ -1,12 +1,13 @@
|
|||
---
|
||||
title: MISP 2.4.61 released
|
||||
date: 2017-01-22
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.61](https://github.com/MISP/MISP/tree/v2.4.61) has been released, including a critical bug fix, new features and minor updates. We strongly recommend to update MISP to this latest version.
|
||||
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
|
||||
[Warning lists](https://github.com/MISP/misp-warninglists) has been significantly updated with two new types: ```hostname``` and ```substring```. This allows
|
||||
to make more granular matching to find additional potential false-positives. The ```hostname``` type allows smart substring matching within URLs.
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.62 and PyMISP 2.4.62 released
|
||||
date: 2017-01-26
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.62](https://github.com/MISP/MISP/tree/v2.4.62) has been released, including bug fixes and new features.
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.63 released
|
||||
date: 2017-02-01
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.63](https://github.com/MISP/MISP/tree/v2.4.63) has been released, including bug fixes and new features.
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.65 released
|
||||
date: 2017-02-09
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.65](https://github.com/MISP/MISP/tree/v2.4.65) (and 2.4.64) has been released, including bug fixes and new features.
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: Sighting the next level
|
||||
date: 2017-02-16
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
Sighting is an [endless topic of discussion](https://lists.oasis-open.org/archives/cti-stix/201508/msg00019.html). This is a required feature especially when information or indicators are regularly shared to gather feedback from users said shared data. Adequate sightings can be an incredible source of information in order to describe the life-time of an indicator, its evolution and especially to ensure the understanding of indicators among a group of users using the information to detect, mitigate or block malicious activities in their infrastructures. The potential is endless, potentially being a significant gain for organised communities of infosec professionals sharing information or even serve as a requirement for advanced algorithms ranging from machine learning to reinforcement learning. But to reach such a state of a feedback loop, you first require a functional model of sighting.
|
||||
|
|
@ -26,7 +27,7 @@ MISP 2.4.66 has been released including the improved sightings feature. As you c
|
|||
|
||||
<div class="myvideo">
|
||||
<video style="display:block; width:100%; height:auto;" autoplay controls loop="loop">
|
||||
<source src="{{ site.baseurl }}/assets/images/misp/video/sighting.webm" type="video/webm" />
|
||||
<source src="{{ site.baseurl }}/img/blog/misp/video/sighting.webm" type="video/webm" />
|
||||
</video>
|
||||
</div>
|
||||
|
||||
|
|
@ -1,14 +1,15 @@
|
|||
---
|
||||
title: MISP 2.4.67 released
|
||||
date: 2017-02-24
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.67](https://github.com/MISP/MISP/tree/v2.4.67) has been released, including improvements to the sighting feature, user management and activity visualisation.
|
||||
|
||||
Sighting activities over tags and galaxy clusters are now visualised using sparklines, giving us an interesting outlook of contextual activity:
|
||||
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
|
||||
Advanced sighting activity is now available at the event level to view the summary of sightings submitted at the attribute level.
|
||||
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.68 released
|
||||
date: 2017-03-08
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.68](https://github.com/MISP/MISP/tree/v2.4.68) has been released including multiple bug fixes and improvements.
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.69 released
|
||||
date: 2017-03-10
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.69](https://github.com/MISP/MISP/tree/v2.4.69) has been released including multiple security bug fixes and minor improvements.
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.70 released
|
||||
date: 2017-03-26
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.70](https://github.com/MISP/MISP/tree/v2.4.70) has been released including new features, improvements and important bug fixes.
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.71 released
|
||||
date: 2017-04-11
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.71](https://github.com/MISP/MISP/tree/v2.4.71) has been released including new features, improvements and important bug fixes.
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.72 released
|
||||
date: 2017-04-14
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.72](https://github.com/MISP/MISP/tree/v2.4.72) has been released including improvements and important bug fixes.
|
||||
|
|
@ -1,14 +1,15 @@
|
|||
---
|
||||
title: MISP 2.4.73 released
|
||||
date: 2017-05-09
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.73](https://github.com/MISP/MISP/tree/v2.4.73) has been released including new features, improvements and bug fixes.
|
||||
|
||||
A new module type Cortex has been introduced allowing for easy integration of MISP and Cortex. [Cortex](https://github.com/CERT-BDF/Cortex) is the analysis engine part of the [TheHive Project](https://thehive-project.org/) which supports expansion services from Cortex within MISP. A new setting has been added to support Cortex similarly to MISP expansion modules where you set the remote Cortex instance. MISP includes a new Cortex attribute type to allow for the raw analysis to be stored along with the event for subsequent analysis.
|
||||
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
|
||||
The MISP feed handling was reworked to expand the functionality and avoid the past limitation:
|
||||
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.74 released
|
||||
date: 2017-05-30
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.74](https://github.com/MISP/MISP/tree/v2.4.74) has been released including new features, improvements and bug fixes.
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.75 released
|
||||
date: 2017-06-13
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.75](https://github.com/MISP/MISP/tree/v2.4.75) has been released including bug fixes and a set of performance improvements.
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.76 released
|
||||
date: 2017-06-21
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.76](https://github.com/MISP/MISP/tree/v2.4.76) has been released including bug fixes and a set of performance improvements at the ingestion level.
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.77 released
|
||||
date: 2017-07-12
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.77](https://github.com/MISP/MISP/tree/v2.4.77) has been released including security fixes, bug fixes and various improvements.
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.78 released
|
||||
date: 2017-08-06
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.78](https://github.com/MISP/MISP/tree/v2.4.77) has been released including an important security fix (if you use sharing groups), multiple bug fixes and some new functionalities.
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.79 released
|
||||
date: 2017-08-25
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.79](https://github.com/MISP/MISP/tree/v2.4.79) has been released including an important security fix (persistent XSS on comment field), multiple bug fixes and new functionalities.
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.80 released (aka MISP objects release)
|
||||
date: 2017-09-18
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.80](https://github.com/MISP/MISP/tree/v2.4.80) has been released including the most awaited [MISP objects](https://github.com/MISP/misp-objects) feature along with other new features, security fix [CVE-2017-14337](https://www.circl.lu/advisory/CVE-2017-14337/) and improvements.
|
||||
|
|
@ -19,7 +20,7 @@ The default MISP object templates included are: ail-leak, cookie, credit-card, d
|
|||
|
||||
An example which describes a DGA (Domain Generation Algorithm) linked to two domain indicators using the MISP object functionality:
|
||||
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
|
||||
Relationships can be described from an existing list of relationship types (e.g. `executed-by`, `impersonates`, `communicates-with`,...) or by values from your own relationship vocabulary. This allows to
|
||||
model a fairly large set of cases from incident, collected intelligence, attacks or course-of-action to malware analysis.
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.81 released (aka new graphical visualisation and STIX 2.0 export)
|
||||
date: 2017-09-18
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.81](https://github.com/MISP/MISP/tree/v2.4.81) has been released including a significant rework of the graphical visualisation, support for STIX 2.0 export, multiple bug-fixes and improvements for misp-objects.
|
||||
|
|
@ -11,7 +12,7 @@ The new correlation graph has been improved and now includes the correlation at
|
|||
The navigation and expansion within the correlation graph has now a series of shortcut keys (`q` and `e`) to quickly navigate within large graphs. There is also a new contextual information pane,
|
||||
to quickly show the currently selected and hovered nodes. This improves the navigation over large graphs and quickly expands the information from the selected nodes.
|
||||
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
|
||||
STIX 2.0 is now supported as an export format in this release. Even though the STIX 2.0 format is still unpublished and at an early stage, we decided to implement a first export tool to see the gaps of
|
||||
the format and helps our users to test the export with potential tools which start to support the version 2.0. As MISP commitment is to support the maximum of format, STIX 1.1 has been also expanded
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.82 released (aka improved pub-sub ZMQ)
|
||||
date: 2017-11-10
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.82](https://github.com/MISP/MISP/tree/v2.4.82) has been released including an improved publish-subscribe ZMQ format, improvements in the feeds system, sightings are now ingested and synchronised among MISP instances, many bug fixes and export improvements.
|
||||
|
|
@ -11,7 +12,7 @@ to deliver additional information to the subscribers. The system can be used to
|
|||
|
||||
<div class="myvideo">
|
||||
<video style="display:block; width:100%; height:auto;" autoplay controls loop="loop">
|
||||
<source src="{{ site.baseurl }}/assets/images/misp/video/misp-zmq-dashboard-integration.mp4" type="video/mp4" />
|
||||
<source src="{{ site.baseurl }}/img/blog/misp/video/misp-zmq-dashboard-integration.mp4" type="video/mp4" />
|
||||
</video>
|
||||
</div>
|
||||
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.83 released (aka attributes-level tag filtering and more)
|
||||
date: 2017-12-06
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.83](https://github.com/MISP/MISP/tree/v2.4.83) has been released including attribute level tag filtering on synchronisation, full audit logging via ZMQ or Syslog, user email domain restriction at the org level, many more improvements and bug fixes.
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.85 released (aka feeds and warning-lists improvement and more)
|
||||
date: 2017-12-22
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.85](https://github.com/MISP/MISP/tree/v2.4.85) has been released including improvements to the feed ingestion performance, warning-list handling and many bug fixes.
|
||||
|
|
@ -25,7 +26,7 @@ Improvement and cleanup in the event index:
|
|||
|
||||
Various UI improvements to clean up the interface for the analysts, including changes such as the collapse of attributes with highly correlating events:
|
||||
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
|
||||
The advanced sighting view on objects is now properly working.
|
||||
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: Using MISP to share vulnerability information efficiently
|
||||
date: 2018-01-09
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/vul02.png
|
||||
banner: /img/blog/vul02.png
|
||||
---
|
||||
|
||||
# Using MISP to share vulnerability information efficiently
|
||||
|
|
@ -26,18 +27,18 @@ Sharing a set of vulnerabilities to a trusted group is straightforward. First yo
|
|||
vulnerabilities and assign the corresponding sharing group. An event is just a container with meta-data associated with it such as a classification
|
||||
or a generic description.
|
||||
|
||||

|
||||

|
||||
|
||||
Then when your event is created, the event can be used to attach attributes or objects. If you want to share vulnerability information,
|
||||
a vulnerability object can be added to describe the vulnerability.
|
||||
|
||||

|
||||

|
||||
|
||||
The vulnerability object is composed of various attributes such as the vulnerable configuration expressed as a CPE value and can be added multiple times if you have different vulnerable configurations.
|
||||
|
||||

|
||||

|
||||
|
||||

|
||||

|
||||
|
||||
Another effective aspect when pre-sharing vulnerability within MISP is to benefit from the Globally Unique Identifier allocation (GUID) for each attributes. This allows to share efficiently without the need to allocate unique identifier. If a CVE allocation is done after, this has no impact on the event when the vulnerability identifiers are set.
|
||||
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.86 released (aka sharing groups improvement, large information sharing communities support and more)
|
||||
date: 2018-01-16
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.86](https://github.com/MISP/MISP/tree/v2.4.86) has been released including improvements to the sharing groups and their respective APIs, granular access control of MISP-modules at an instance-level along with the usual set of bug fixes.
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.87 released (aka translate everything, improvements everywhere and more)
|
||||
date: 2018-01-28
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.87](https://github.com/MISP/MISP/tree/v2.4.87) has been released including a massive contribution enabling support for internationalisation and localisation in the MISP UI (a huge thank to Steve Clement of CIRCL for the tedious work), as well as a host of improvements to the UI, feed and APIs, including bug fixes and speed improvements.
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.88 released (aka Fuzzy hashing correlation, STIX 1.1 import and many API improvements)
|
||||
date: 2018-02-21
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.88](https://github.com/MISP/MISP/tree/v2.4.88) has been released including fuzzy hashing correlation (ssdeep), STIX 1.1 import functionality, various API improvements and many bug fixes
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.89 released (aka Event graph viewer/editor)
|
||||
date: 2018-03-23
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.89](https://github.com/MISP/MISP/tree/v2.4.89) has been released including a new MISP event graph viewer/editor, many API improvements and critical bug fixes (including security related bug fixes).
|
||||
|
|
@ -10,7 +11,7 @@ We introduced a new functionality allowing analysts and MISP users to view objec
|
|||
|
||||
<div class="myvideo">
|
||||
<video style="display:block; width:100%; height:auto;" autoplay controls loop="loop">
|
||||
<source src="{{ site.baseurl }}/assets/images/misp/video/event-graph.webm" type="video/webm" />
|
||||
<source src="{{ site.baseurl }}/img/blog/misp/video/event-graph.webm" type="video/webm" />
|
||||
</video>
|
||||
</div>
|
||||
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: Introducing The New Extended Events Feature in MISP
|
||||
date: 2018-04-19
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
# Introducing Extended Events
|
||||
|
|
@ -27,13 +28,13 @@ To create an extension event, simply enter the UUID or ID of the event in the "E
|
|||
|
||||
Users viewing the original report, will now see a new field called "Extended by" as shown below:
|
||||
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
|
||||
Clicking on the atomic view / extended view toggle button will allow you to jump from the classical event view to the extended event view. The extended view will add all of the relations, tags, galaxy clusters, attributes and objects of the extender events. The attribute list in extended view also shows the event it originates from along with the creator organisation. Keep in mind that duplicates across several events are not culled.
|
||||
|
||||
Extending an event is easy and a nifty lookup interface helps you to select the appropriate event to extend:
|
||||
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
|
||||
In the above case, OSINT information contained within an event is extended with additional threat hunting information which are limited to your organisation. The major advantage of such an approach is allowing any organisation to expand information without touching the original event.
|
||||
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.90 released (aka Extended Events release)
|
||||
date: 2018-04-20
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.90](https://github.com/MISP/MISP/tree/v2.4.90) has been released including the new extended events feature along with many updates in improvements in the API, user-interface (including many improvement in the graph editor) and many bug fixes.
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.91 released (aka distribution visualisation, galaxy at attribute level and privacy notice list)
|
||||
date: 2018-05-16
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.91](https://github.com/MISP/MISP/tree/v2.4.91) has been released including new major features, improvements and bug fixes.
|
||||
|
|
@ -13,14 +14,14 @@ become quite larger, with long lists of objects and attributes, analysts need to
|
|||
allows them to view the items per distribution level including the associated sharing groups. The visualisation is dynamic and can be used to
|
||||
filter the given attributes matching a specific distribution setting within the event.
|
||||
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
|
||||
### Galaxy at attribute level
|
||||
|
||||
[MISP Galaxy](/galaxy.html) includes a large number of libraries to assist in classifying events based on threat actors, kill chains or actor techniques such as described in the [MITRE ATT&CK](https://attack.mitre.org/wiki/Main_Page) galaxy. Initially, MISP galaxies were limited to be attached to MISP events alone. As many users developed new galaxy cluster to map their own model, MISP 2.4.91 is now capable of attaching MISP clusters at the attribute level. In the example below, a vulnerability attribute can be then easily linked to the respective MITRE ATT&CK adversary technique supporting analysts trying to search for and pivot on techniques, but also supporting various more advanced automation scenarios.
|
||||
|
||||
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
|
||||
### Privacy notice list and GDPR
|
||||
|
||||
|
|
@ -30,11 +31,11 @@ In MISP 2.4.91, we introduced the [MISP notice system](https://github.com/MISP/m
|
|||
|
||||
We expect to see organisations using MISP to enable, disable or extend the notice lists to fit their specific policies, legal frameworks or local regulation frameworks.
|
||||
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
|
||||
and notice lists are easily configurable:
|
||||
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
|
||||
### API
|
||||
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.92 released (aka performance improvement)
|
||||
date: 2018-06-07
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.92](https://github.com/MISP/MISP/tree/v2.4.92) has been released including aggressive performance boosts, various improvements and bug fixes.
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.93 released (aka ATT&CK integration)
|
||||
date: 2018-06-27
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.93](https://github.com/MISP/MISP/tree/v2.4.93) has been released including a much improved and tightly integrated [MITRE ATT&CK](https://attack.mitre.org) interface, a new event locking functionality, initial support for a multilingual interface, various fixes including a security fix ([CVE-2018-12649](https://cve.circl.lu/cve/CVE-2018-12649)).
|
||||
|
|
@ -10,7 +11,7 @@ MITRE ATT&CK offers an excellent, efficient and very complete framework to descr
|
|||
|
||||
<div class="myvideo">
|
||||
<video style="display:block; width:100%; height:auto;" autoplay controls loop="loop">
|
||||
<source src="{{ site.baseurl }}/assets/images/misp/video/attack.webm" type="video/webm" />
|
||||
<source src="{{ site.baseurl }}/img/blog/misp/video/attack.webm" type="video/webm" />
|
||||
</video>
|
||||
</div>
|
||||
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.94 released (aka summer improvements)
|
||||
date: 2018-08-06
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP [2.4.94](https://github.com/MISP/MISP/tree/v2.4.94) has been released including an improved event graph interface, a new Elasticsearch plugin, various extensions and enhancements to the API, clean-ups and many improvements. Even though it's summertime, we continuously work on the MISP project and a lot of changes were introduced.
|
||||
|
|
@ -11,13 +12,13 @@ Major improvements have been implemented in the MISP event graph such as:
|
|||
- Export functionality added in the MISP event graph to export in PNG, JPEG, JSON format and Graphviz dot format.
|
||||
- Saving functionality to save the state of an event graph. This allows a user of an organisation to keep the state of the event graph and retrieve the history.
|
||||
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
|
||||
The MITRE ATT&CK matrix user-interface has been extended to add directly techniques at event level without passing by the galaxy interface.
|
||||
|
||||
A new functionality contributed allows users to log all MISP activities in Elasticsearch. It's pretty simple to configure thanks to its settings being part of the standard plugin settings system, so head over there to find the Elasticsearch configuration options.
|
||||
|
||||

|
||||

|
||||
|
||||
The CLI interface has been improved with the ability to get the API key of a given user, to force update the taxonomies, warning lists, notice lists and object templates. All of this serves to improve the automation of deployment of MISP instances without the need to use the UI.
|
||||
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.95 released (aka API search improvement)
|
||||
date: 2018-09-06
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP ([2.4.95](https://github.com/MISP/MISP/tree/v2.4.95)) has been released with the first stage of a complete rework and refactoring of the API exports, allowing for more flexibility, improved search capabilities, performance and extendability.
|
||||
|
|
@ -38,7 +39,7 @@ A debug functionality has been added in any API query to quickly show the SQL qu
|
|||
|
||||
Many new [MISP modules](https://www.github.com/MISP/misp-modules) were included and we extend MISP to better support enrichment modules with large output (such as the Sigma to search queries converter). In this version, a new on-demand pop-up has been introduced to have a sticky hover to ease cut-and-paste or selection.
|
||||
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
|
||||
A bro NIDS type has been added in MISP to support the exchange of raw bro NIDS signature within MISP communities.
|
||||
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.96 released (aka API everywhere release)
|
||||
date: 2018-10-09
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP ([2.4.96](https://github.com/MISP/MISP/tree/v2.4.96)) has been released with a complete rework, refactoring and simplification of the restSearch API, allowing for more flexibility, improved search capabilities, performance and extendability.
|
||||
|
|
@ -1,16 +1,17 @@
|
|||
---
|
||||
title: MISP 2.4.97 released (aka so many new features)
|
||||
date: 2018-10-30
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP ([2.4.97](https://github.com/MISP/MISP/tree/v2.4.97)) has been released with new features such as related tags, the sighting restSearch API, a new French localisation along with many improvements to the API and he import/export capabilities, such as improved support for [DHS AIS](https://www.us-cert.gov/ais) STIX 1 files.
|
||||
|
||||
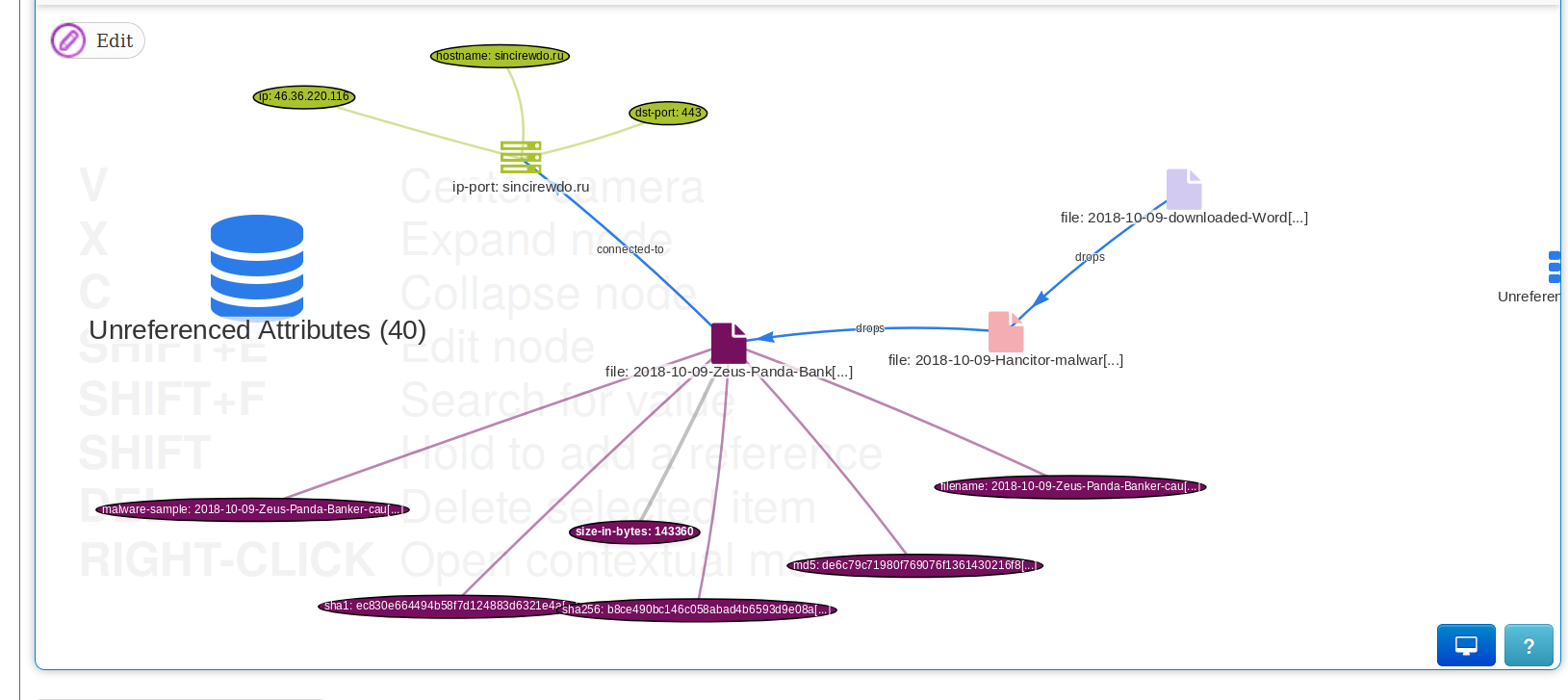
|
||||
|
||||
|
||||
The new related tags functionality has been introduced to allow users to view the most commonly used tags for a specific attribute across all events. This can help analysts when deciding to use a specific classification based on previous analyses to reduce the time it takes to contextualise the new information.
|
||||
|
||||
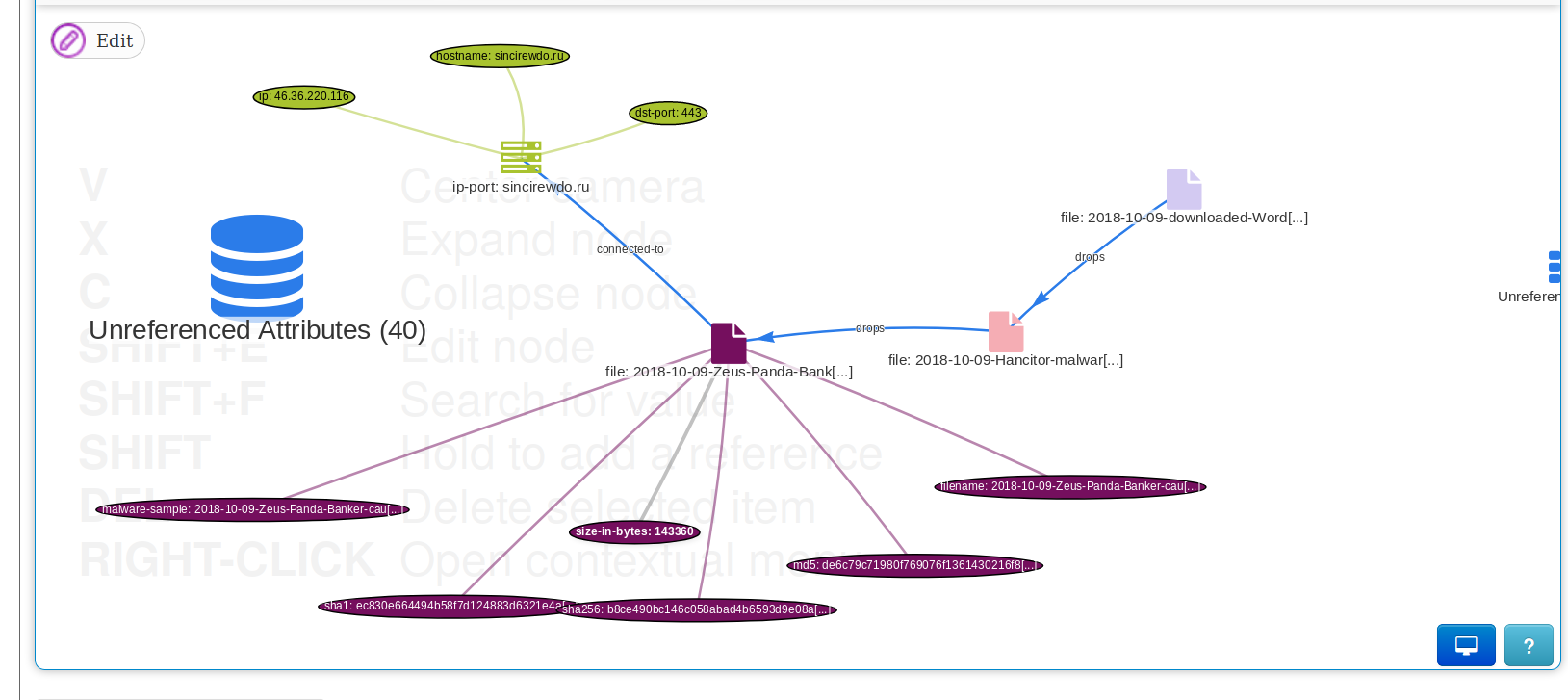
|
||||
|
||||
|
||||
A new API has been introduced, allowing users to search [MISP sightings](https://www.misp.software/2017/02/16/Sighting-The-Next-Level.html) using a set of filter parameters along with a list of data formats (JSON, CSV or XML). The search is available on an event, attribute or instance level. You can easily search by time ranges (from, to or last) using the standard restSearch API syntax.
|
||||
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.98 released (aka usability improvements and SleuthKit mactime import)
|
||||
date: 2018-11-26
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP ([2.4.98](https://github.com/MISP/MISP/tree/v2.4.98)) has been released with new features such as improved UI consistency (such as attributes search output), improved validation error messages, a new built-in experimental SleuthKit mactime import, new small features and many bugs fixed.
|
||||
|
|
@ -13,8 +14,8 @@ The output of the search interface is now consistent with standard attributes vi
|
|||
|
||||
A new experimental import functionality has been included to import SleuthKit mactime timelines from MISP directly. The user can import one or more mactime timelines in MISP, which will be included as a mactime object to describe forensic activities on an analysed file system. The import is a two-step process where the user can cherry pick the forensic events which took place and select the meaningful activity to be added in a MISP event.
|
||||
|
||||
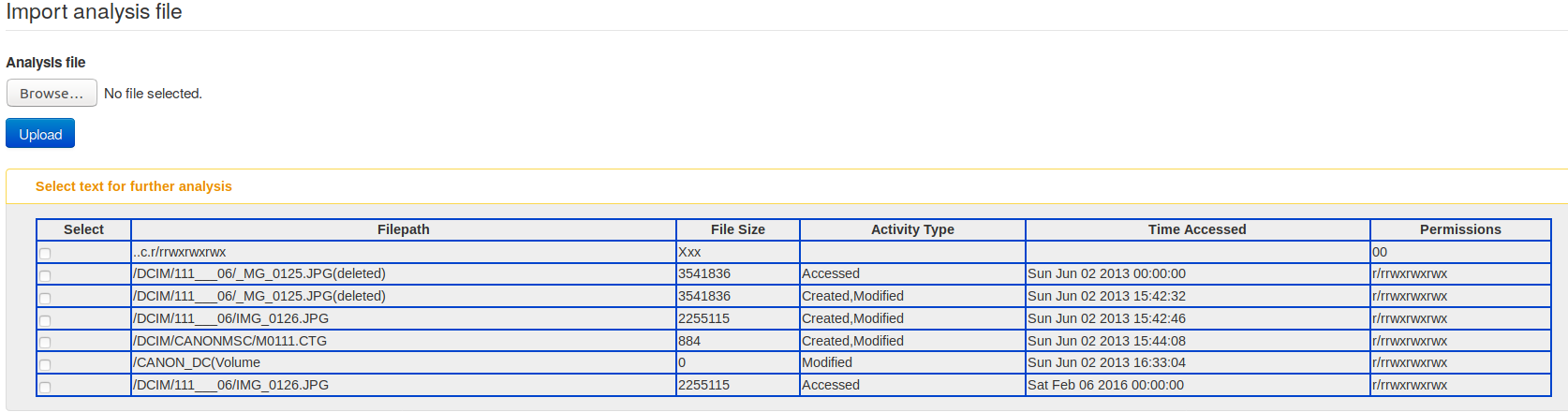
|
||||
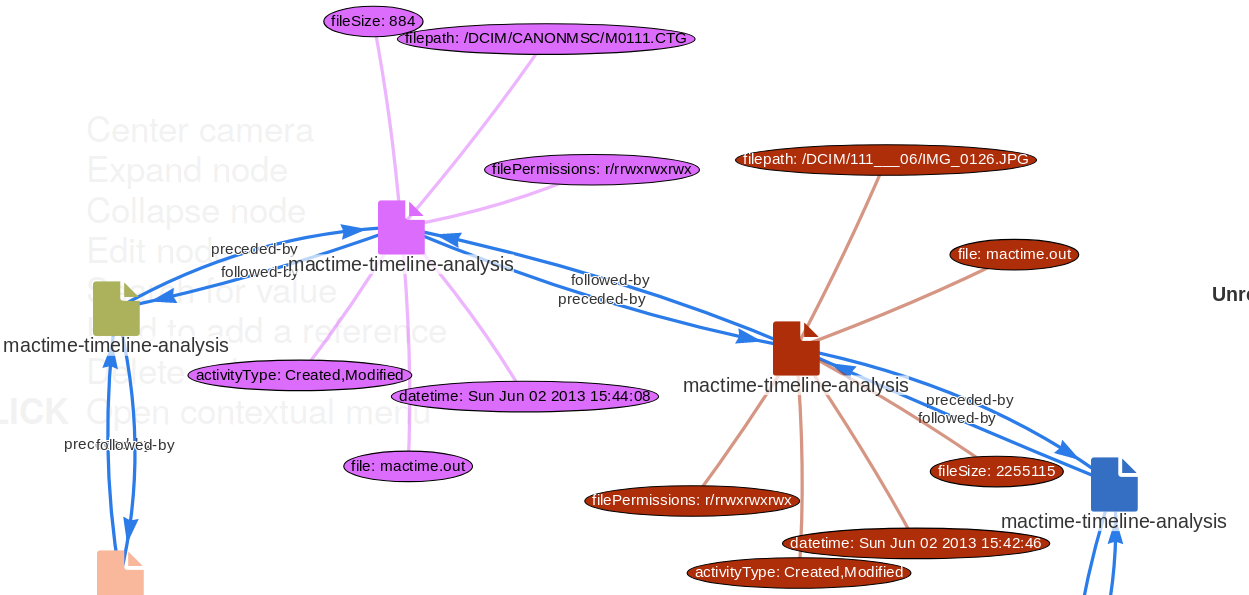
|
||||
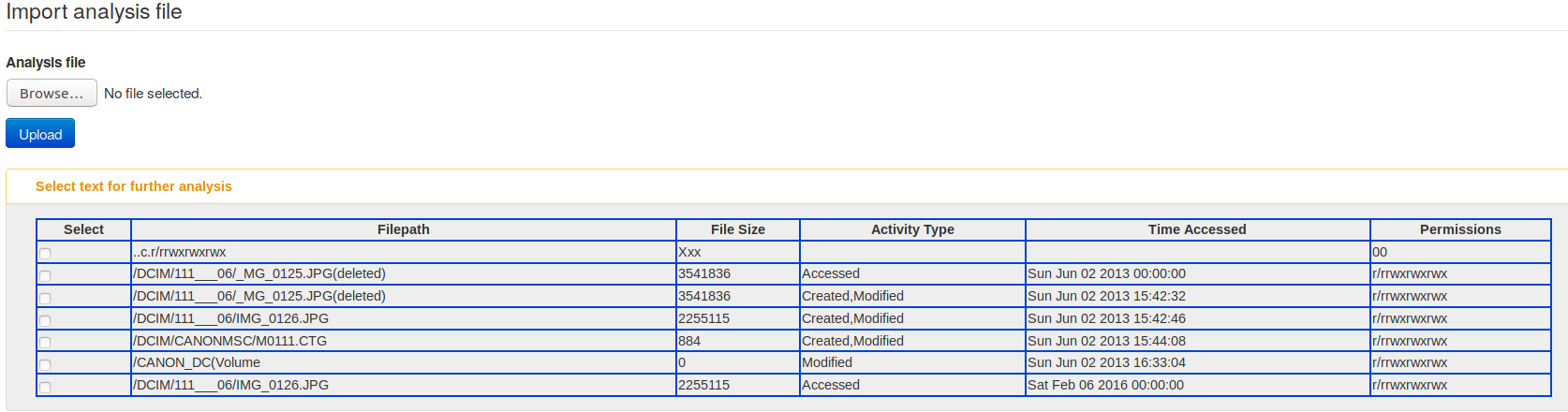
|
||||
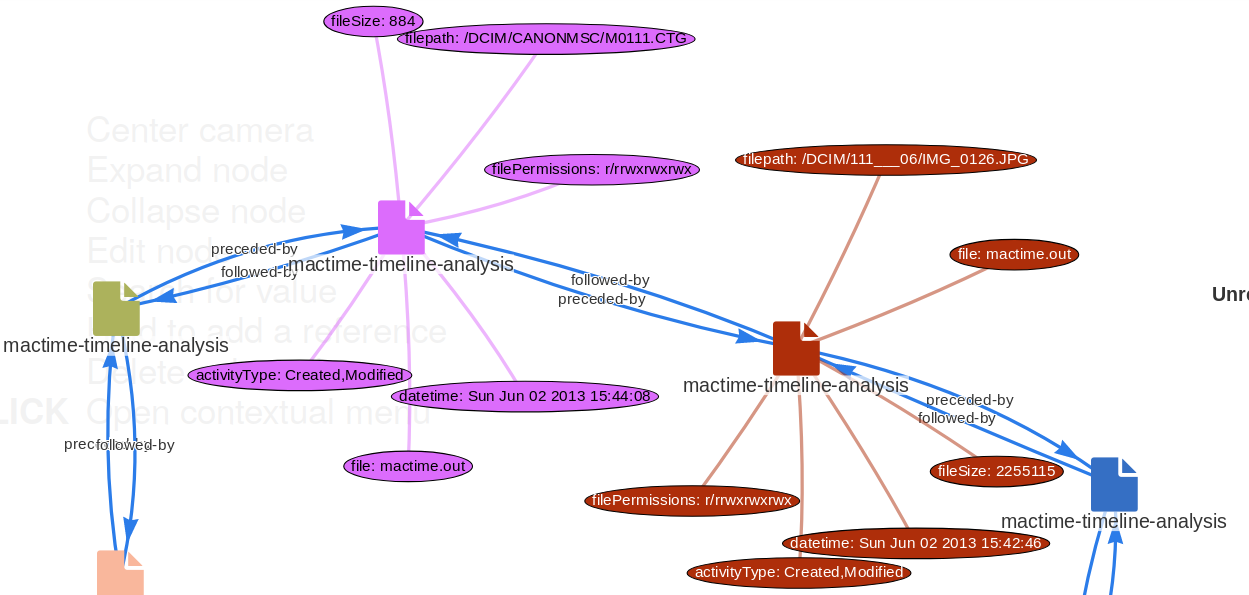
|
||||
|
||||
The API has been improved with many new features such as:
|
||||
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.99 released (aka API/UI fixes and critical security vulnerability fixed)
|
||||
date: 2018-12-06
|
||||
layout: post
|
||||
featured: /assets/images/misp-small.png
|
||||
banner: /img/blog/misp-small.png
|
||||
---
|
||||
|
||||
A new version of MISP ([2.4.99](https://github.com/MISP/MISP/tree/v2.4.99)) has been released with improvements in the UI, API, STIX import and a fixed critical security vulnerability.
|
||||
|
|
@ -1,14 +1,15 @@
|
|||
---
|
||||
title: MISP 2.4.100 released (aka happy new year release)
|
||||
date: 2019-01-01
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/restsearchbuilder.png
|
||||
banner: /img/blog/restsearchbuilder.png
|
||||
---
|
||||
|
||||
Happy new year! We are so proud of our community which has supported us for the past year and we hope to do even better for 2019. Thanks a lot.
|
||||
|
||||
A new version of MISP ([2.4.100](https://github.com/MISP/MISP/tree/v2.4.100)) has been released with improvements to the UI, API, import and export along with the addition of a new query builder.
|
||||
|
||||

|
||||

|
||||
|
||||
Considering the criticality of being able to accurately define how we query MISP instances in order to feed and integrate with network security devices, endpoint security devices or monitoring tools, we have tried to improve the life of the users tasked with the above duties via a new query builder, available through the REST client interface (REST client below the Event Actions). The query builder provides a simple interface to create your JSON queries used to get
|
||||
the information you truly are interested in back for ingestion in your devices and tools easily.
|
||||
|
|
@ -1,20 +1,21 @@
|
|||
---
|
||||
title: MISP 2.4.101 released (aka 3 features for free)
|
||||
date: 2019-01-20
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/tag-collection-creation.png
|
||||
banner: /img/blog/tag-collection-creation.png
|
||||
---
|
||||
|
||||
A new version of MISP ([2.4.101](https://github.com/MISP/MISP/tree/v2.4.101)) has been released with 3 main new features (tag collections, improved tag/galaxy selector and MISP instance caching), along with a host of improvements and bug fixes.
|
||||
|
||||
## Tag collections
|
||||
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
|
||||
Contextualisation in threat intelligence is one of the key activities when performing analysis and when reviewing or processing information from internal or external sources. The task can be rather tedious, but nevertheless, it's a critical step in ensuring the quality and the information's capacity to be used for automatic processing. MISP 2.4.101 introduces a new concept, in an attempt to improve the "time-to-contextualise" information for users using the platform. Tag collections, a new feature in 2.4.101, aim to allow users to predefine re-usable structures consisting of a set of tags (from taxonomies) along with galaxy information attached. Analysts can use these named collections to quickly classify information with all of the contextualisation labels declared in the collection. This functionality enables anyone using MISP to significantly lower the time it takes to classify information and to ensure that all the pre-defined context related information is attached to an event or attribute. This feature is a first step in opening up the sharing of analysisMISP best practices directly via the platform itself.
|
||||
|
||||
## Improved tag/galaxy selector
|
||||
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
|
||||
The success of MISP taxonomies and galaxies since their inception has been suffering from a minor but annoying drawback. When we originally designed the user-interfaces of the tag and galaxy systems in MISP, our immediate intent was to handle a rather small set of taxonomies. Since then we have come a long way and thanks to the many excellent contributions we've received from the community, the ugly side-effect of our original design decisions reared its head: adding multiple tags and galaxies has become a tedious chore, especially when trying to contextualise several aspects of the information to be shared, using multiple tags and galaxies.
|
||||
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.102 released (aka bug fixes and FOSDEM release)
|
||||
date: 2019-02-02
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/anon-graph.png
|
||||
banner: /img/blog/anon-graph.png
|
||||
---
|
||||
|
||||
A new version of MISP ([2.4.102](https://github.com/MISP/MISP/tree/v2.4.102)) has been released with several fixes, various UI improvements, new types and a praise to the open source community.
|
||||
|
|
@ -12,9 +13,9 @@ A new version of MISP ([2.4.102](https://github.com/MISP/MISP/tree/v2.4.102)) ha
|
|||
|
||||
Sharing and exchanging information encompasses a lot of different models, communities or practices, with the MISP project being involved in various discussions and projects centered around building sharing and information exchange communities. A complex topic comes up regularly, namely the anonymisation of the information exchanged. Sharing anonymised information often aims to simply share the existence of knowledge about information. We introduced a new attribute type in MISP called "anonymised", which can be combined with a newly introduced object called [anonymisation](https://www.misp-project.org/objects.html#_anonymisation).
|
||||
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
|
||||
The design is flexible and can be extended with new anonymisation techniques and/or approaches. We are standing on the shoulders of giants, for example open source tools such as [Crypto-PAn](https://www.cc.gatech.edu/computing/Networking/projects/cryptopan/), [ipsumpdump](https://github.com/kohler/ipsumdump) or [arx](https://arx.deidentifier.org/).
|
||||
|
||||
|
|
@ -25,7 +26,7 @@ The open source NIDS [Bro project was renamed Zeek](https://blog.zeek.org/2018/1
|
|||
|
||||
## Sighting
|
||||
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
|
||||
- MISP UI has been improved to allow sighting at the attribute level or at the global level.
|
||||
- Various improvements to the sighting hover such as a generic hovering support.
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.103 released (aka UI improvements)
|
||||
date: 2019-03-04
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/filtering.png
|
||||
banner: /img/blog/filtering.png
|
||||
---
|
||||
|
||||
A new version of MISP ([2.4.103](https://github.com/MISP/MISP/tree/v2.4.103)) has been released with significant UI improvements (including a new flexible attribute filtering tool at the event level), many bug fixes and a fix to a security vulnerability (CVE-2019-9482) which was affecting sighting visibility.
|
||||
|
|
@ -12,9 +13,9 @@ A new version of MISP ([2.4.103](https://github.com/MISP/MISP/tree/v2.4.103)) ha
|
|||
|
||||
A new attribute filtering tool has been added to the event view to replace the previous filtering. Complex filtering rules can be set to easily filter, navigate and paginate over large events with many attributes and objects.
|
||||
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
|
||||
{:class="img-responsive"}
|
||||
{:class="img-responsive"}
|
||||
|
||||
## Improved hover behavior for expansion services.
|
||||
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.104 released (aka too many new features)
|
||||
date: 2019-03-26
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/distribution-graph.png
|
||||
banner: /img/blog/distribution-graph.png
|
||||
---
|
||||
|
||||
A new version of MISP ([2.4.104](https://github.com/MISP/MISP/tree/v2.4.104)) has been released with a host of new features such as new overlap feed comparator, a new graph visualisation of event and attribute distributions, a history/bookmark system for the REST client and many others.
|
||||
|
|
@ -12,20 +13,20 @@ A new version of MISP ([2.4.104](https://github.com/MISP/MISP/tree/v2.4.104)) ha
|
|||
|
||||
Cached feeds can now be compared to the entire set or a subset of the other cached feeds, assisting users in their decision making process for acquiring new feeds based on being able to cover the contents of the new feed with their combination nof existing ingested feeds.
|
||||
|
||||

|
||||

|
||||
|
||||
## Distribution graph
|
||||
|
||||
A new distribution visualisation graph has been introduced to quickly display the potential recipients of the data. This allows users to get an overview of how far events and attributes will be distributed and shows the members of the community who will receive the information shared.
|
||||
|
||||

|
||||

|
||||
|
||||
## Bookmark and history in REST client
|
||||
|
||||
The MISP UI REST Client now keeps a history of the 10 most recently performed queries. Additionally, queries can now be recalled and bookmarked for later use, so there's no longer a need to manually keep track of your queries in your notes,
|
||||
it's now in your MISP instance.
|
||||
|
||||

|
||||

|
||||
|
||||
## Required taxonomy
|
||||
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.105 released (aka security fix for CVE-2019-10254)
|
||||
date: 2019-03-28
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/distribution-graph.png
|
||||
banner: /img/blog/distribution-graph.png
|
||||
---
|
||||
|
||||
A new version of MISP ([2.4.105](https://github.com/MISP/MISP/tree/v2.4.105)) has been released to fix a security vulnerability ([CVE-2019-10254](https://cve.circl.lu/cve/CVE-2019-10254)) in addition to some minor improvements and a fix for the STIX 1.1 import, enabling the import of files with additional namespaces (such as [CISCP](https://www.dhs.gov/cisa/cyber-information-sharing-and-collaboration-program-ciscp)).
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.106 released (aka Too many improvements)
|
||||
date: 2019-04-25
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/graph-thumb.png
|
||||
banner: /img/blog/graph-thumb.png
|
||||
---
|
||||
|
||||
A new version of MISP ([2.4.106](https://github.com/MISP/MISP/tree/v2.4.106)) has been released with a host of improvements, including new features such as a feed cache search, CLI tools to manage your MISP instance along with improved diagnostics.
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.107 released (aka similar objects review, yara native export)
|
||||
date: 2019-05-13
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/similar-objects.png
|
||||
banner: /img/blog/similar-objects.png
|
||||
---
|
||||
|
||||
A new version of MISP ([2.4.107](https://github.com/MISP/MISP/tree/v2.4.107)) has been released with a host of new features, improvements and security fixes. We strongly advise all users to update their MISP installation to this latest version.
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.108 released (aka copy-paste-and-sync feature)
|
||||
date: 2019-06-05
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/anothergraph.png
|
||||
banner: /img/blog/anothergraph.png
|
||||
---
|
||||
|
||||
A new version of MISP ([2.4.108](https://github.com/MISP/MISP/tree/v2.4.108)) has been released with a host of new features, improvements and bugs fixed. We strongly advise all users to update their MISP installations to this latest version.
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.109 released (aka cool-attributes-to-object)
|
||||
date: 2019-06-14
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/attribute-to-object.gif
|
||||
banner: /img/blog/attribute-to-object.gif
|
||||
---
|
||||
|
||||
# MISP 2.4.109 released
|
||||
|
|
@ -12,14 +13,14 @@ A new version of MISP ([2.4.109](https://github.com/MISP/MISP/tree/v2.4.109)) ha
|
|||
|
||||
## Encapsulate existing attributes into an object
|
||||
|
||||
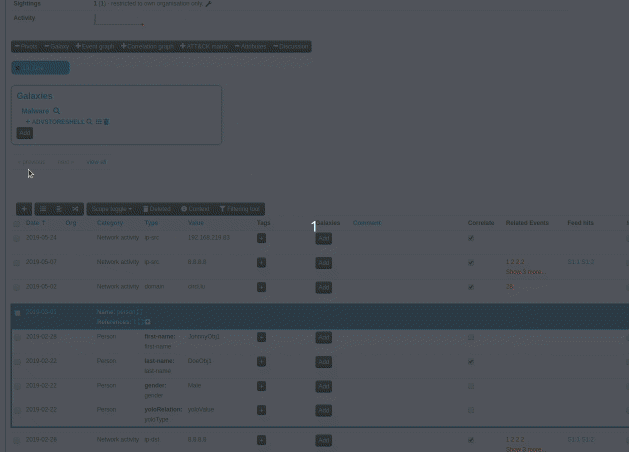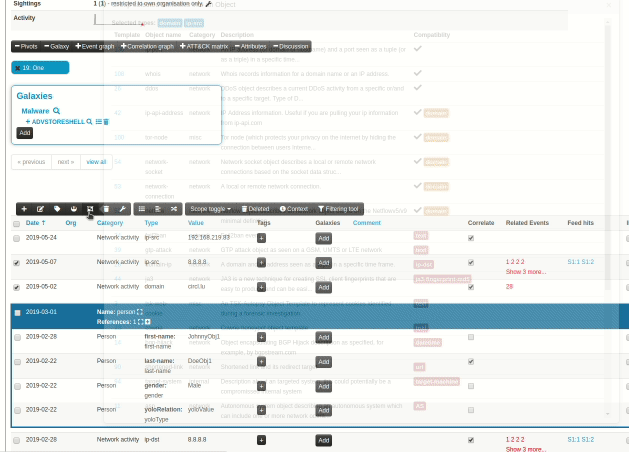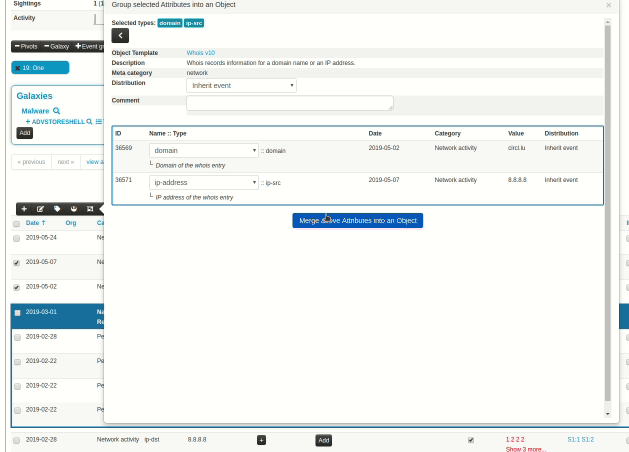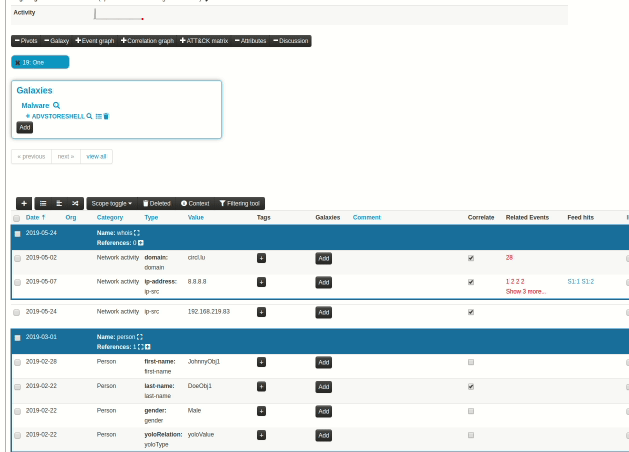
|
||||
|
||||
|
||||
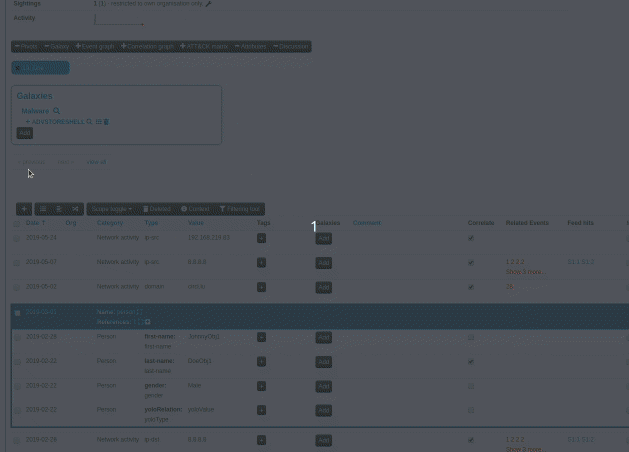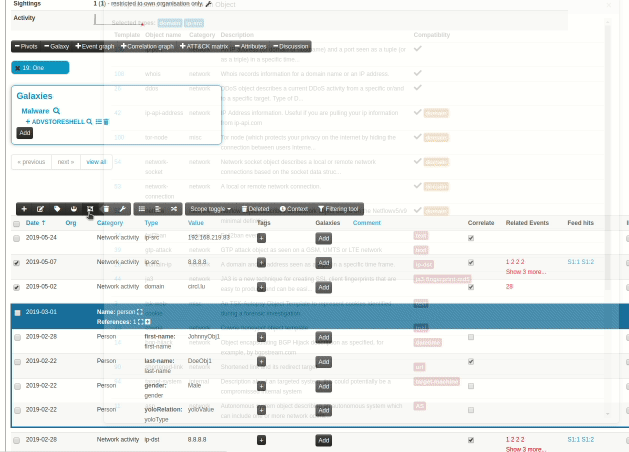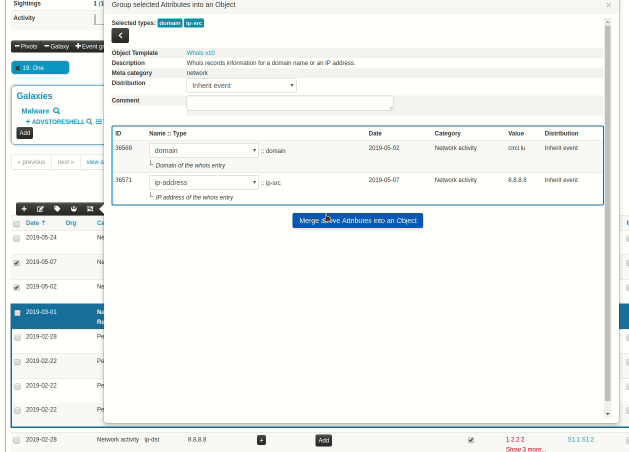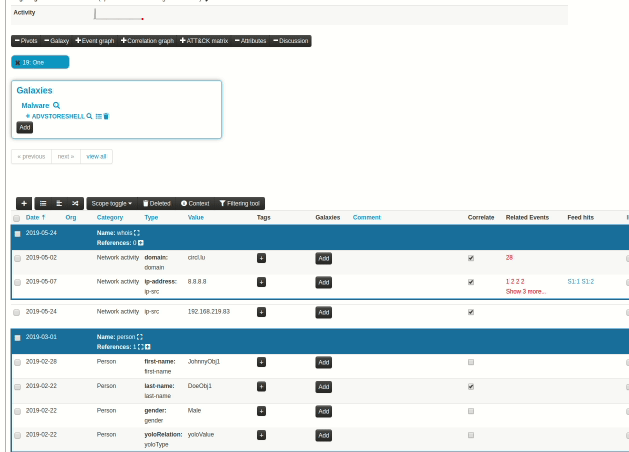
When an analyst inserts information into MISP, it's very common to start with a set of unstructured indicators/attributes. At a later stage, common structures emerge and combining attributes into objects start making more and more sense. However, the effort spent on the process of attribute creation would have to be repeated in prior versions via the object creation interface, something that resulted in analysts deciding to save time and effort and move on, leaving the unstructured data as is. To reduce the workload needed to bring structure to our prior work, we have now introduced a new feature, allowing users to easily select a set of attributes and automatically propose suitable object templates depending on the combination of types of the selected attributes. These in turn, can be gathered and processed into the desired object.
|
||||
|
||||
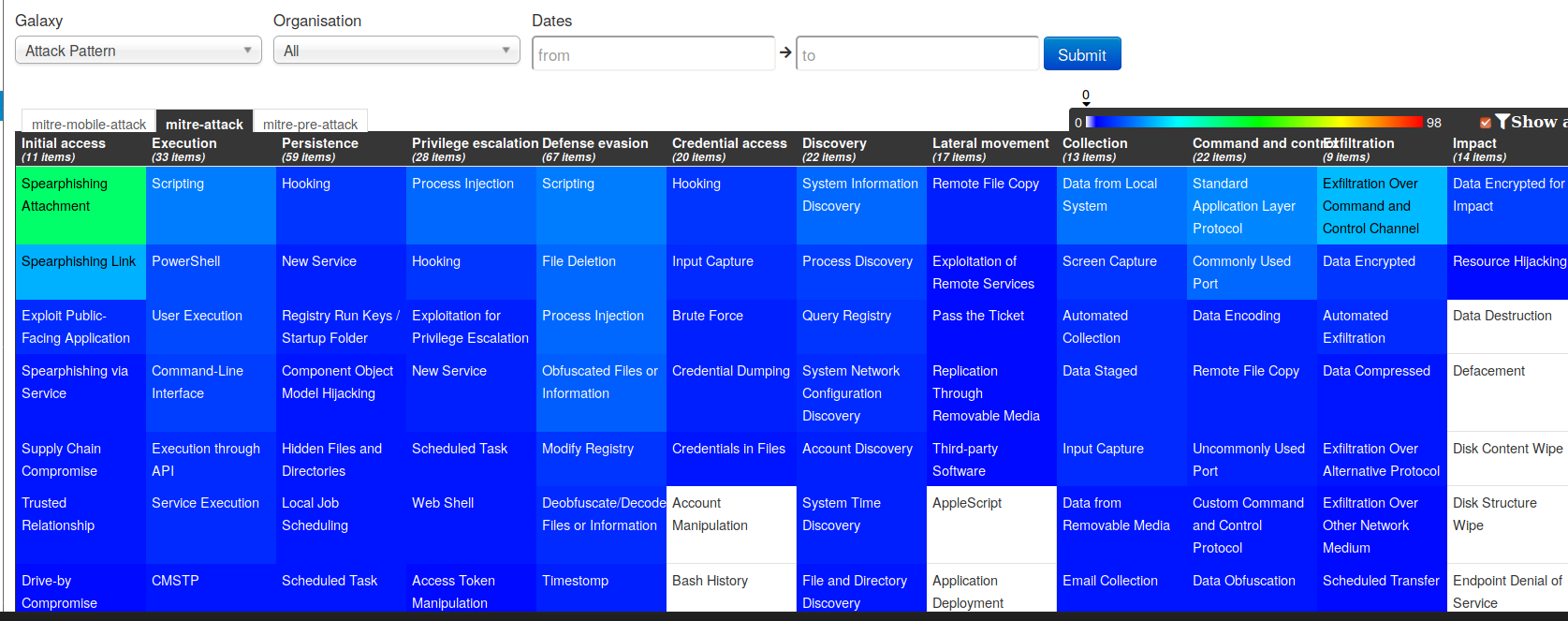
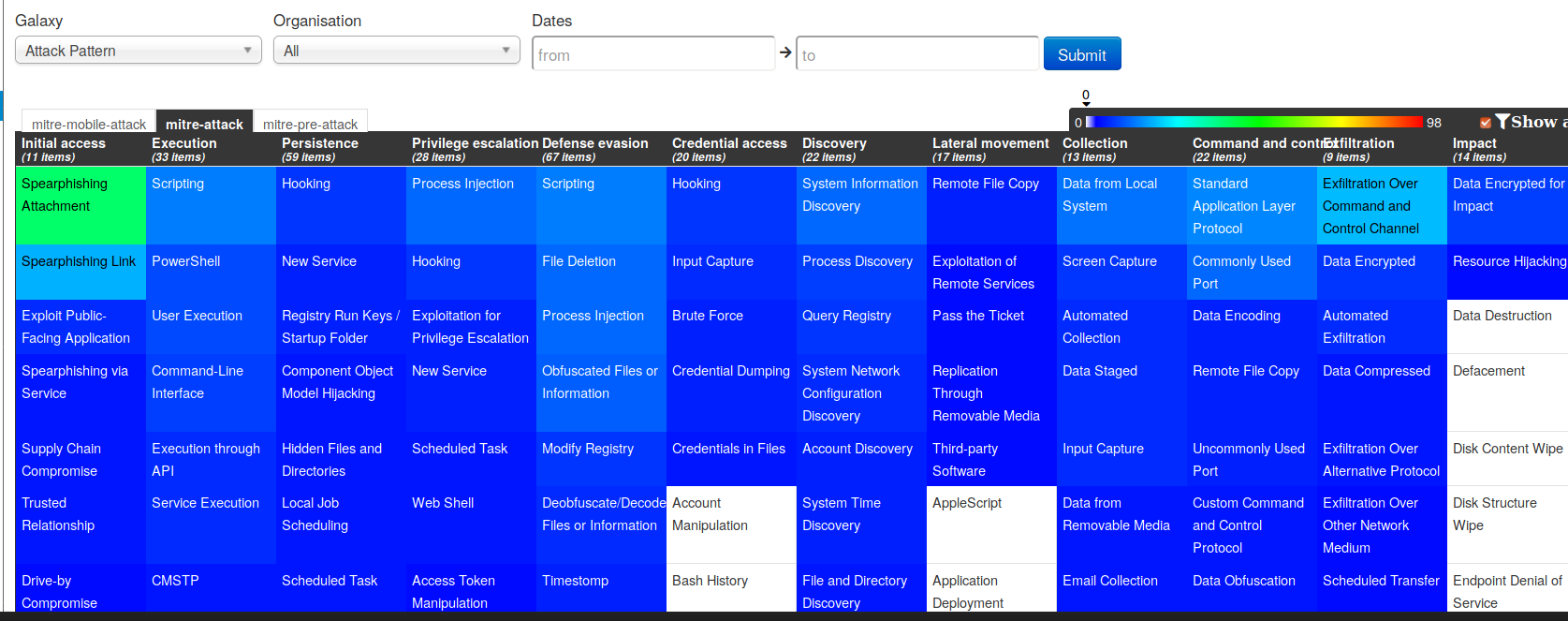
## Improved ATT&CK and ATT&CK-like matrix support
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
We received exhaustive feedback during the FIRST.org CTI conference in London and the [ATT&CK EU community](https://www.attack-community.org/) workshop at Eurocontrol concerning the ATT&CK integration in MISP. The matrix visualisation has been improved by sorting and reorganising the individual techniques based on their aggregate scores. These statistics can now easily be queried based on time-ranges, organisations, tags, along with all other restSearch enabled filters to generate ATT&CK like matrix views.
|
||||
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.110 released (aka local-tags and new MISP modules supporting MISP standard format)
|
||||
date: 2019-07-08
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/modules-expand.gif
|
||||
banner: /img/blog/modules-expand.gif
|
||||
---
|
||||
|
||||
# MISP 2.4.110 released
|
||||
|
|
@ -14,12 +15,12 @@ A new version of MISP ([2.4.110](https://github.com/MISP/MISP/tree/v2.4.110)) ha
|
|||
|
||||
[misp-modules](https://github.com/MISP/misp-modules) now support MISP objects and relationships. The revamped system is still compatible with the old modules, whilst the new modules bolster up the complete MISP standard format. New modules such as [url-haus](https://github.com/MISP/misp-modules/blob/52dadd2df32b19241fdd978e50b717f1967e264b/misp_modules/modules/expansion/urlhaus.py), [joe sandbox query](https://github.com/MISP/misp-modules/blob/be61613da4f5dc8f082a7c1a9e1ec07fdb872560/misp_modules/modules/expansion/joesandbox_query.py) and many others support the new MISP standard format. This new feature allows module developers to create more advanced modules, generating MISP objects and associated relationships from any type of expansion, import or export modules in one click.
|
||||
|
||||
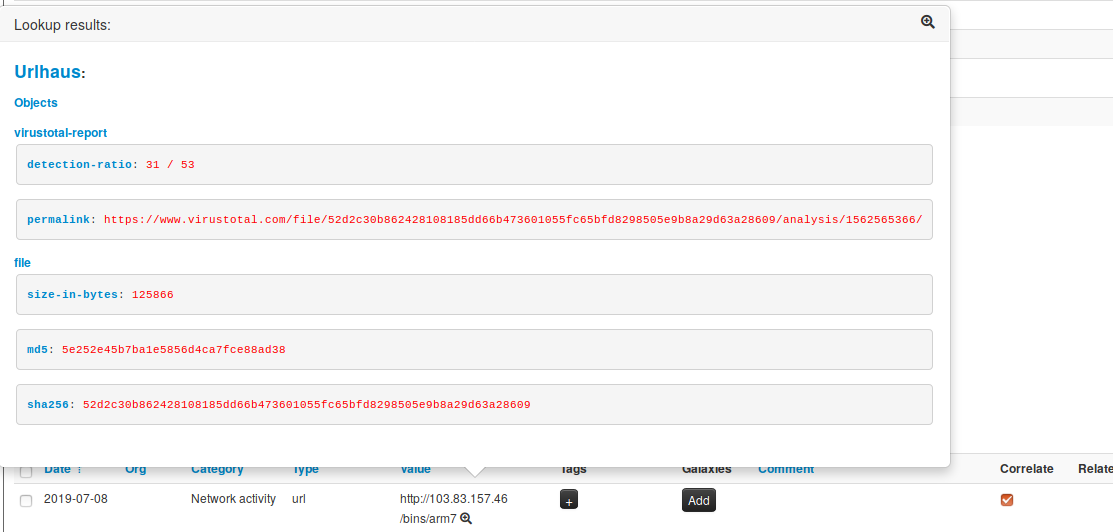
|
||||
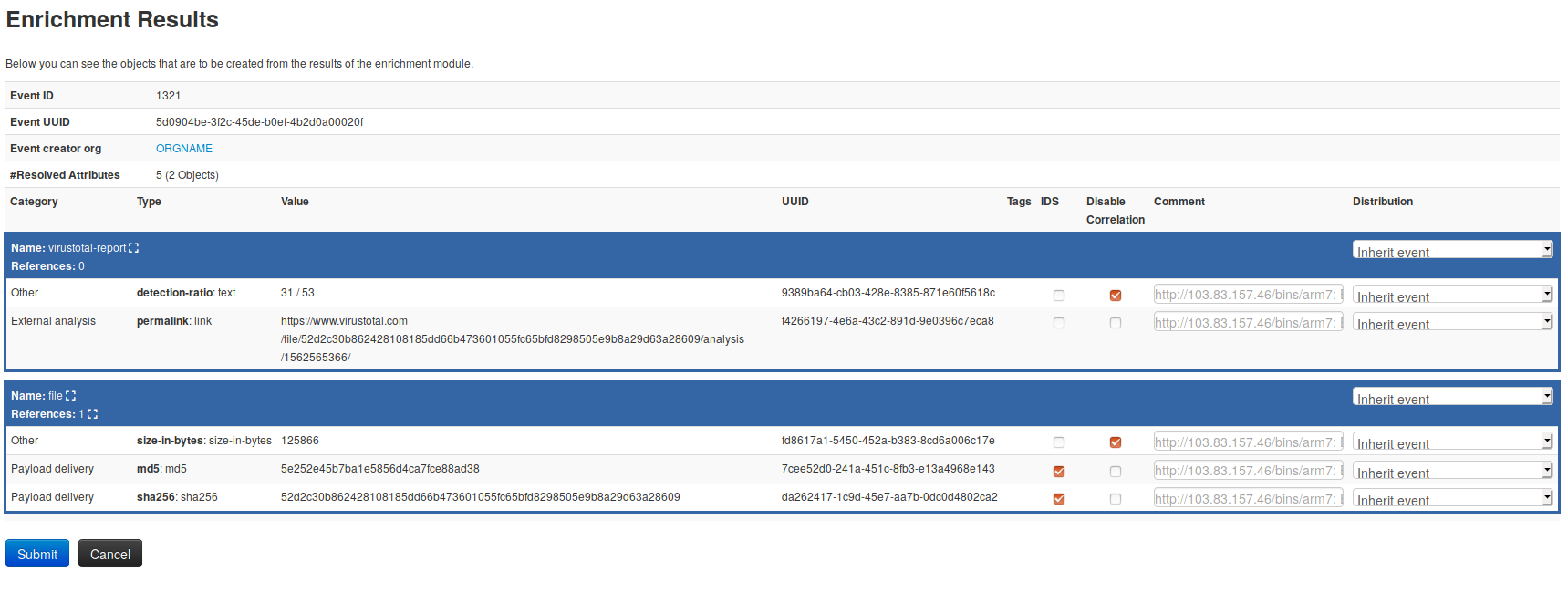
|
||||
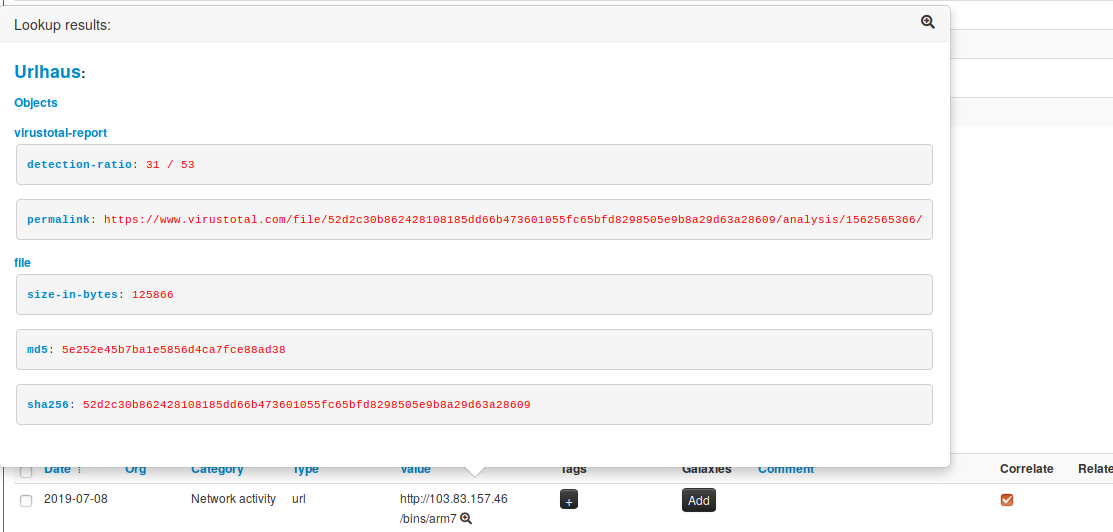
|
||||
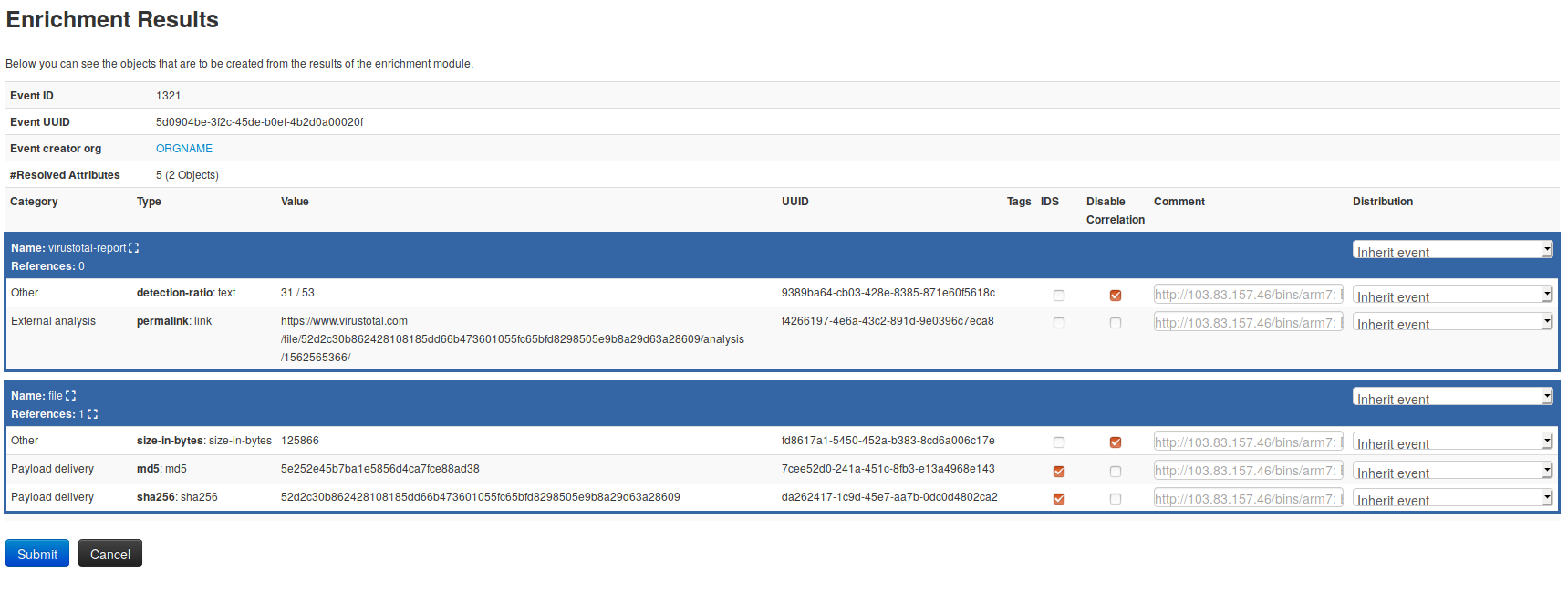
|
||||
|
||||
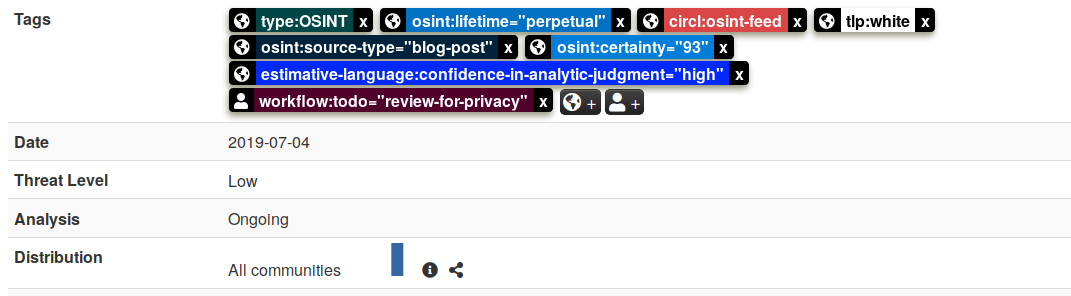
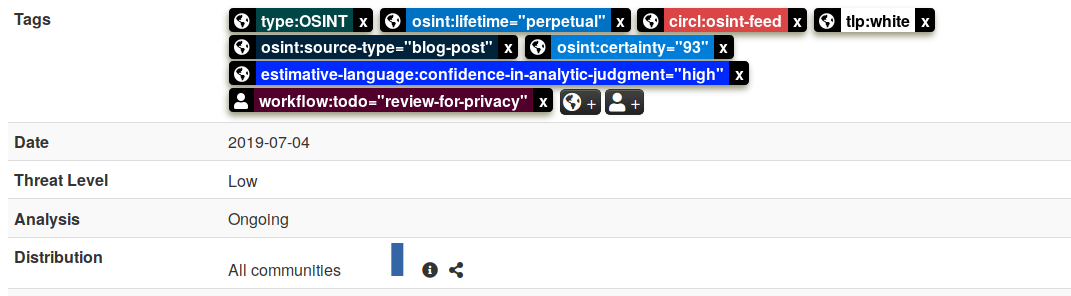
## Local tags introduced
|
||||
|
||||
|
||||
|
||||
|
||||
The long awaited feature "local tags" is now finally available. You can create tags locally if you are a member of the given MISP instance's host organisation, enabling "in-place" tagging for synchronisation and export filtering. MISP events are not modified while using the local tags and are in turn always stripped before being synchronised with other MISP instances and sharing communities. Local tags allow users to avoid violating the ownership model of MISP, but still be able to tag any event or attribute for further dissemination and data contextualisation. Local tagging works for tags, tag collections, galaxies and matrix-like galaxies such as ATT&CK.
|
||||
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.111 released (aka improved proposal sync)
|
||||
date: 2019-07-19
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/comid.jpeg
|
||||
banner: /img/blog/comid.jpeg
|
||||
---
|
||||
|
||||
# MISP 2.4.111 released
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.112 released (aka summer fixes and improvement)
|
||||
date: 2019-08-01
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/vuln.png
|
||||
banner: /img/blog/vuln.png
|
||||
---
|
||||
|
||||
# MISP 2.4.112 released
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.113 released (aka the bugs fixing marathon)
|
||||
date: 2019-08-19
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/matrix.jpg
|
||||
banner: /img/blog/matrix.jpg
|
||||
---
|
||||
|
||||
# MISP 2.4.113 released
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.114 released (aka the community care package release)
|
||||
date: 2019-08-31
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/community-view.png
|
||||
banner: /img/blog/community-view.png
|
||||
---
|
||||
|
||||
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.115 released (aka CVE-2019-16202 and sync speed improvement)
|
||||
date: 2019-09-10
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/community-view.png
|
||||
banner: /img/blog/community-view.png
|
||||
---
|
||||
|
||||
# MISP 2.4.115 released
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: Decaying of Indicators - MISP improved model to expire indicators based on custom models
|
||||
date: 2019-09-12
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/decay.png
|
||||
banner: /img/blog/decay.png
|
||||
---
|
||||
|
||||
# An improved and flexible model to expire indicators
|
||||
|
|
@ -36,9 +37,9 @@ We still have to see how the ``base_score`` is actually computed. In the current
|
|||
|
||||
To give the intuition of how the ``base_score`` computation works, let's look at two examples. In these examples, the two *Taxonomies* used are
|
||||
[*phishing*](https://github.com/MISP/misp-taxonomies/blob/master/phishing/machinetag.json) and [*admiralty-scale*](https://github.com/MISP/misp-taxonomies/blob/master/admiralty-scale/machinetag.json). Both of them contain *Tags* that have a ``numerical_value`` associated to them:
|
||||
- <img src="/assets/images/misp/blog/decaying//tag-as-A.png" alt="admiraly-scale:source-reliability = Completely reliable" width="300"/>, ``numerical_value = 100``
|
||||
- <img src="/assets/images/misp/blog/decaying//tag-as-D.png" alt="admiraly-scale:source-reliability = Not usually reliable" width="300"/>, ``numerical_value = 25``
|
||||
- <img src="/assets/images/misp/blog/decaying//tag-p-H.png" alt="phishing:psychological-acceptability = high" width="250"/>, ``numerical_value = 75``
|
||||
- <img src="/img/blog/decaying//tag-as-A.png" alt="admiraly-scale:source-reliability = Completely reliable" width="300"/>, ``numerical_value = 100``
|
||||
- <img src="/img/blog/decaying//tag-as-D.png" alt="admiraly-scale:source-reliability = Not usually reliable" width="300"/>, ``numerical_value = 25``
|
||||
- <img src="/img/blog/decaying//tag-p-H.png" alt="phishing:psychological-acceptability = high" width="250"/>, ``numerical_value = 75``
|
||||
|
||||
So, if an *Attribute* only has a single *Tag* attached, for example ``admiralty-scale:source-reliability="Completely reliable"``, the ``base_score`` would be:
|
||||
```
|
||||
|
|
@ -53,9 +54,9 @@ phishing = 50
|
|||
---------------------
|
||||
sum 100
|
||||
```
|
||||
If an *Attribute* has the *Tags* <img src="/assets/images/misp/blog/decaying/tag-as-A.png" alt="admiraly-scale:source-reliability = Completely reliable" width="300"/> and <img src="/assets/images/misp/blog/decaying/tag-p-H.png" alt="phishing:psychological-acceptability = high" width="250"/> attached, the computation steps would look like this:
|
||||
If an *Attribute* has the *Tags* <img src="/img/blog/decaying/tag-as-A.png" alt="admiraly-scale:source-reliability = Completely reliable" width="300"/> and <img src="/img/blog/decaying/tag-p-H.png" alt="phishing:psychological-acceptability = high" width="250"/> attached, the computation steps would look like this:
|
||||
|
||||

|
||||

|
||||
|
||||
Thus, the ``base_score`` of this *Attribute* will be ``87.50``.
|
||||
|
||||
|
|
@ -70,7 +71,7 @@ Now that we've seen the basic concepts, let's have a look at how MISP implements
|
|||
|
||||
At the *Event* level, a new filter button has been added, which attaches the real-time computed ``score`` to all *Attributes* that have been mapped to a *Model*.
|
||||
|
||||
<img src="/assets/images/misp/blog/decaying/dm-event.png" alt="Decay Model index" width="700"/>
|
||||
<img src="/img/blog/decaying/dm-event.png" alt="Decay Model index" width="700"/>
|
||||
|
||||
### Endpoint: ``attribute/restSearch``
|
||||
|
||||
|
|
@ -109,19 +110,19 @@ When creating a new *Decaying Model*, modifying its parameters and viewing the o
|
|||
|
||||
### Customising the lifetime and the decay speed parameters
|
||||
|
||||
<video src="/assets/images/misp/blog/decaying/dm-tool.mp4" title="Decaying Model Fine Tuning Tool - Parameters" width="800" height="450" controls autoplay loop>
|
||||
<video src="/img/blog/decaying/dm-tool.mp4" title="Decaying Model Fine Tuning Tool - Parameters" width="800" height="450" controls autoplay loop>
|
||||
Your browser does not support the video tag.
|
||||
</video>
|
||||
|
||||
### Setting the ``base_score``: Customising Taxonomies' weights
|
||||
|
||||
<video src="/assets/images/misp/blog/decaying/dm-bs.mp4" type="video/mp4" title="Decaying Model Fine Tuning Tool - Base score" width="800" height="450" controls autoplay loop>
|
||||
<video src="/img/blog/decaying/dm-bs.mp4" type="video/mp4" title="Decaying Model Fine Tuning Tool - Base score" width="800" height="450" controls autoplay loop>
|
||||
Your browser does not support the video tag.
|
||||
</video>
|
||||
|
||||
### Viewing scores and simulating the model
|
||||
|
||||
<video src="/assets/images/misp/blog/decaying/dm-simulation.mp4" type="video/mp4" title="Decaying Model Simulation Tool" width="800" height="450" controls autoplay loop>
|
||||
<video src="/img/blog/decaying/dm-simulation.mp4" type="video/mp4" title="Decaying Model Simulation Tool" width="800" height="450" controls autoplay loop>
|
||||
Your browser does not support the video tag.
|
||||
</video>
|
||||
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.116 released (aka the new decaying feature)
|
||||
date: 2019-09-17
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/decay.png
|
||||
banner: /img/blog/decay.png
|
||||
---
|
||||
|
||||
# MISP 2.4.116 released
|
||||
|
|
@ -14,7 +15,7 @@ After several years of gathering requirements, doing [research](https://arxiv.or
|
|||
|
||||
The feature allows MISP users to have a simple yet customisable system to automatically (or in some cases semi-manually) mark an Indicator Of Compromise (or more generally, an Attribute) as expired. The expiration system allows for the overlaying of computed scores on all attributes in real-time, based on the configured mappings via a decay model. The feature has been designed not to change the attributes per se, but rather to extend the meta information available about the attributes. As with everything in MISP, this new feature is accessible via both the user-interface and also via the API, in order to allow for the filtering of attributes based on a decay model.
|
||||
|
||||
<img src="/assets/images/misp/blog/decaying/dm-event.png" alt="Decay Model index" width="700"/>
|
||||
<img src="/img/blog/decaying/dm-event.png" alt="Decay Model index" width="700"/>
|
||||
|
||||
The feature is exhaustive and we highly recommend to read the [blog post and watch the video showing all aspects of the new feature](https://www.misp-project.org/2019/09/12/Decaying-Of-Indicators.html) or [the slides from the MISP training](https://www.misp-project.org/misp-training/a.5-decaying-indicators.pdf). As usual, MISP comes with a set of default decay models which can be extended locally or contributed back to the community at large.
|
||||
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: Benefits of running your own MISP instance
|
||||
date: 2019-09-25
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/community-view.png
|
||||
banner: /img/blog/community-view.png
|
||||
---
|
||||
|
||||
# Benefits of running your own MISP instance
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.117 released (aka the the pre-conference season release)
|
||||
date: 2019-10-11
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/decay.png
|
||||
banner: /img/blog/decay.png
|
||||
---
|
||||
|
||||
# MISP 2.4.117 released
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: Visualising common patterns using MISP and ATT&CK data
|
||||
date: 2019-10-27
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/visualisation_cylance_attack/actor_delta.png
|
||||
banner: /img/blog/visualisation_cylance_attack/actor_delta.png
|
||||
---
|
||||
|
||||
# Visualising common patterns using MISP and ATT&CK data
|
||||
|
|
@ -21,7 +22,7 @@ You will want to download the [Maltego CE](https://www.paterva.com/buy/maltego-c
|
|||
|
||||
## The report
|
||||
As an example, when looking at the report of attacks called "[PcShare Backdoor Attacks Targeting Windows Users with FakeNarrator Malware](https://threatvector.cylance.com/en_us/home/pcshare-backdoor-attacks-targeting-windows-users-with-fakenarrator-malware.html)", published by Cylance on the 25th of September 2019, and shared using MISP to 'All Communities' with the UUID `5d9b5ad3-6b64-4962-a63c-42ae73e10023`. They also attributed the attack to the [Tropic Trooper - G0081](https://attack.mitre.org/groups/G0081/) actor.
|
||||

|
||||

|
||||
|
||||
## Analysis and Visualisation
|
||||
In addition to the technical report of these attacks and the leveraged malware, the author documented 16 related ATT&CK techniques. Interestingly MITRE associated 18 ATT&CK techniques to this actor.
|
||||
|
|
@ -33,17 +34,17 @@ Keeping in mind the limitations of our working memory (7±2 items) we will need
|
|||
|
||||
**Open Maltego** and create a **MISPEvent entity** with the MISP event number on your MISP server (for me this is `63423`). **Right click** on the event and choose **"Event To Galaxies"**.
|
||||
|
||||

|
||||

|
||||
|
||||
We now have a first visual view of the tags that were attached to the report. Now, select the threat actor and choose **Galaxy to Relations** again, in order to expand this using MITRE ATT&CK relationships.
|
||||
We now see a completely new graph which is much less readable. Make sure you configure Maltego to make collections of 4 or more similar entities. You can do this in the toolbar in the top: 
|
||||
We now see a completely new graph which is much less readable. Make sure you configure Maltego to make collections of 4 or more similar entities. You can do this in the toolbar in the top: 
|
||||
|
||||

|
||||

|
||||
|
||||
**Suddenly our graph becomes much more readable and we see at a glance that our initial intuition of two missing techniques was actually completely wrong !**
|
||||
The Cylance report of these attacks does NOT have two (2) techniques fewer than expected. Actually, only five (5) are common with what MITRE documented! Thirteen (13) are only present in the MITRE documentation and eleven (11) are not associated with this actor by MITRE. Zooming in allows us to see the details:
|
||||
|
||||

|
||||

|
||||
|
||||
## What does this mean?
|
||||
Does this mean Cylance or MITRE are wrong?
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.118 released (aka the exclusivity tag release and SightingDB support)
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/exclusive/exclusive-example-1.png
|
||||
banner: /img/blog/exclusive/exclusive-example-1.png
|
||||
date: 2019-11-10
|
||||
---
|
||||
|
||||
# MISP 2.4.118 released
|
||||
|
|
@ -10,10 +11,10 @@ A new version of MISP ([2.4.118](https://github.com/MISP/MISP/tree/v2.4.118)) ha
|
|||
|
||||
# Exclusive taxonomies
|
||||
|
||||
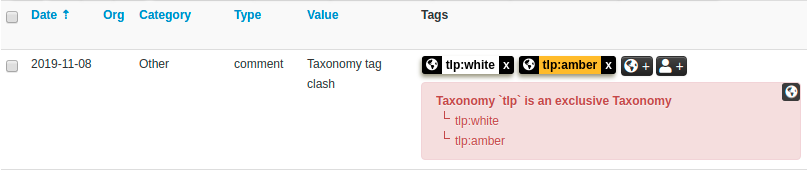
|
||||
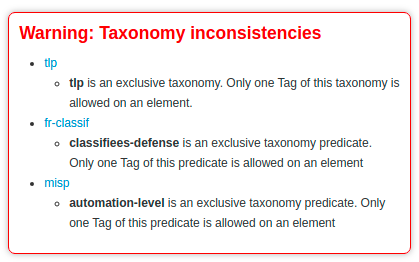
|
||||
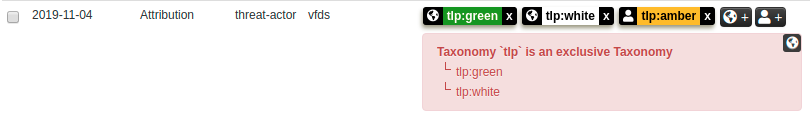
|
||||
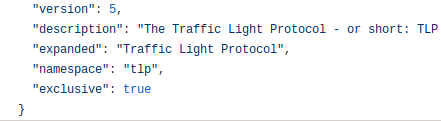
|
||||
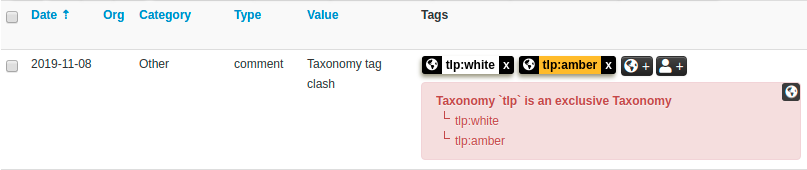
|
||||
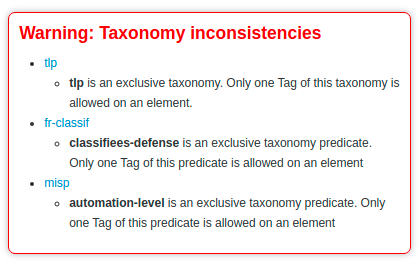
|
||||
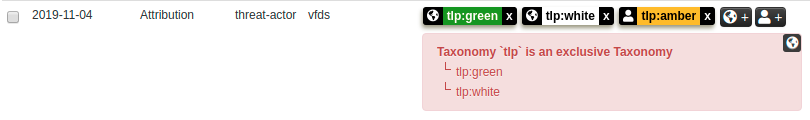
|
||||
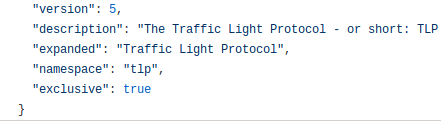
|
||||
|
||||
Some time ago, we've introduced the "exclusive" field in the MISP taxonomy format, in order to define rules of exclusivity within a given taxonomy predicate. As of this release, the MISP user-interface shows and enforces inconsistencies of exclusivity between tags assigned at the event and the attribute levels.
|
||||
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.119 released (aka the quality of life release)
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/119-1.png
|
||||
banner: /img/blog/119-1.png
|
||||
date: 2019-12-04
|
||||
---
|
||||
|
||||
# MISP 2.4.119 released
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.120 released (aka the timeline release)
|
||||
date: 2020-01-21
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/t-misp-overview.png
|
||||
banner: /img/blog/t-misp-overview.png
|
||||
---
|
||||
|
||||
# MISP 2.4.120 released
|
||||
|
|
@ -15,7 +16,7 @@ progress of the update can be verified via the interface of your MISP instance u
|
|||
|
||||
# Timeline feature and improved data-model
|
||||
|
||||
<video src="/assets/images/misp/blog/timeline-video.mp4" title="Overview of the MISP timeline feature" width="800" height="450" controls autoplay loop>Video tag is not supported by your browser</video>
|
||||
<video src="/img/blog/timeline-video.mp4" title="Overview of the MISP timeline feature" width="800" height="450" controls autoplay loop>Video tag is not supported by your browser</video>
|
||||
|
||||
[MISP standard format](https://www.misp-standard.org/) has been extended to support first_seen and last_seen on any attribute or object in a MISP instance. This functionality is fully accessible via the restSearch API and via the user-interface of MISP. first_seen and last_seen can be set at the attribute and/or the object levels. A complete timeline viewer and editor has been added to allow users to:
|
||||
|
||||
|
|
@ -23,7 +24,7 @@ progress of the update can be verified via the interface of your MISP instance u
|
|||
- Zoom in and out in the timeline (alt + mouse wheel);
|
||||
- Edit and change the first_seen and last_seen by moving the attributes/objects directly on the timeline.
|
||||
|
||||

|
||||

|
||||
|
||||
As an example above, a spear phishing attack and their respective occurrences are displayed on the timeline. This new feature allows users to describe complex time-based information whilst using existing features such as object relationships.
|
||||
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.121 released (aka the security release)
|
||||
date: 2020-02-12
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/t-misp-overview.png
|
||||
banner: /img/blog/t-misp-overview.png
|
||||
---
|
||||
|
||||
# MISP 2.4.121 released
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.122 released (aka the bug fix release)
|
||||
date: 2020-02-18
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/t-misp-overview.png
|
||||
banner: /img/blog/t-misp-overview.png
|
||||
---
|
||||
|
||||
# MISP 2.4.122 released
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.123 released (aka the dashboard and security fix release)
|
||||
date: 2020-03-10
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/dashboard.png
|
||||
banner: /img/blog/dashboard.png
|
||||
---
|
||||
|
||||
# MISP 2.4.123 released
|
||||
|
|
@ -6,7 +6,9 @@ authors:
|
|||
date: 2020-03-26
|
||||
tags: ["Disinformation", "Information Operations", "Cognitive Security", "MISP", "Threat Intelligence"]
|
||||
categories: []
|
||||
featured: /assets/images/cogsec/amitt.png
|
||||
banner: /img/blog/cogsec/amitt.png
|
||||
date: 2020-03-27
|
||||
layout: post
|
||||
image:
|
||||
placement: 3
|
||||
caption: ''
|
||||
|
|
@ -44,14 +46,14 @@ At its core MISP is an automated correlation engine. It assists analysts in fin
|
|||
|
||||
## AM!TT Misinformation Pattern Galaxy
|
||||
|
||||

|
||||

|
||||
|
||||
Our first achievement was the integration of the [AM!TT Framework](https://github.com/misinfosecproject/amitt_framework) as a [MISP Galaxy](https://www.misp-project.org/galaxy.html#_misinformation_pattern). It contains the tags and definitions needed for describing the misinformation tactics and techniques present in a specific information operation.
|
||||
|
||||
|
||||
## AM!TT Navigatord
|
||||
|
||||

|
||||

|
||||
|
||||
Applying the AM!TT galaxy information to an event must be easy in order to encourage use by already overburdened information researchers. The MISP Project developers kindly created an inline AM!TT Navigator to respond to this need for conveniently tagging events with AM!TT techniques.
|
||||
|
||||
|
|
@ -60,7 +62,7 @@ With this tool, analysts can simply click on the relevant techniques found in a
|
|||
|
||||
## DFRLab Dichotomies of Disinformation
|
||||
|
||||

|
||||

|
||||
|
||||
Also included in the CogSec Collab MISP is [Atlantic Council's DFRLab](https://www.atlanticcouncil.org/programs/digital-forensic-research-lab/) [Dichotomies of Disinformation](https://github.com/DFRLab/Dichotomies-of-Disinformation) which is a new standard for describing information campaigns that can be used alone or in complement to the AM!TT framework.
|
||||
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.124 released (aka the dashboard, auditing improvements)
|
||||
date: 2020-04-06
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/dashboard.png
|
||||
banner: /img/blog/dashboard.png
|
||||
---
|
||||
|
||||
# MISP 2.4.124 released
|
||||
|
|
@ -11,15 +12,15 @@ A new version of MISP ([2.4.124](https://github.com/MISP/MISP/tree/v2.4.123)) ha
|
|||
# Dashboard and widget improved
|
||||
|
||||
The dashboard has been improved along with a host of bugs fixed. A UI for the multiline widget has been introduced.
|
||||
<img src="/assets/images/misp/blog/2.4.124/multiline-demo.gif" alt="Multiline Demo" width="700"/>
|
||||
<img src="/img/blog/2.4.124/multiline-demo.gif" alt="Multiline Demo" width="700"/>
|
||||
The new interface provides users a simple way to manipulate basic graph components. It includes legends, tooltips, auto-resize, clickable labels and a full support of the 2 most common x-axis: linear and time-based.
|
||||
|
||||
You can query the chart to see the delta between two datapoints by selecting the first then the last points. A summary will then be presented.
|
||||
<img src="/assets/images/misp/blog/2.4.124/multiline-brush-delta.png" alt="Multiline delta between points" width="700"/>
|
||||
<img src="/img/blog/2.4.124/multiline-brush-delta.png" alt="Multiline delta between points" width="700"/>
|
||||
|
||||
|
||||
Finally, the widget styling is largely configurable. In addition to the `time_format` and the abscissa type, you can define other parameter influencing how the graph should be presented to the users
|
||||
<img src="/assets/images/misp/blog/2.4.124/multiline-config.png" alt="Multiline Configuration sample" width="700"/>
|
||||
<img src="/img/blog/2.4.124/multiline-config.png" alt="Multiline Configuration sample" width="700"/>
|
||||
|
||||
# (auditing) Individual user monitoring
|
||||
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.125 released (aka self-registration feature and feed improvements release)
|
||||
date: 2020-05-06
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/timeline-sight.png
|
||||
banner: /img/blog/timeline-sight.png
|
||||
---
|
||||
|
||||
# MISP 2.4.125 released
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.126 released (Spring release edition)
|
||||
date: 2020-06-04
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/dashboard.png
|
||||
banner: /img/blog/dashboard.png
|
||||
---
|
||||
|
||||
# MISP 2.4.126 released
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.127 released (decay updates release edition)
|
||||
date: 2020-06-19
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/decay.png
|
||||
banner: /img/blog/decay.png
|
||||
---
|
||||
|
||||
# MISP 2.4.127 released
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.128 released (STIX import/export refactored release edition)
|
||||
date: 2020-06-24
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/d4_sshd_widget.png
|
||||
banner: /img/blog/d4_sshd_widget.png
|
||||
---
|
||||
|
||||
# MISP 2.4.128 released
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.129 released (merge event improved, event block rule system, security fixes and many bugs fixed)
|
||||
date: 2020-07-28
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/d4_sshd_widget.png
|
||||
banner: /img/blog/d4_sshd_widget.png
|
||||
---
|
||||
|
||||
# MISP 2.4.129 released
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: Publishing open data from MISP
|
||||
date: 2020-07-30
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/opendata.png
|
||||
banner: /img/blog/opendata.png
|
||||
---
|
||||
|
||||
# Publish data on Open data portals with MISP
|
||||
|
|
@ -1,12 +1,13 @@
|
|||
---
|
||||
title: Creating a MISP Galaxy, 101
|
||||
date: 2020-07-31
|
||||
layout: post
|
||||
authors:
|
||||
- Koen Van Impe
|
||||
date: 2020-07-31
|
||||
tags: ["Galaxy", "Cluster", "MISP", "Threat Intelligence"]
|
||||
categories: []
|
||||
featured: /assets/images/galaxy101/galaxy.jpg
|
||||
banner: /img/blog/galaxy101/galaxy.jpg
|
||||
---
|
||||
|
||||
## MISP Galaxies
|
||||
|
|
@ -25,13 +26,13 @@ First some basic concepts
|
|||
- A cluster consists of **elements**, which are the "real" data;
|
||||
- Besides their description and **value**, these elements can contain **synonyms** and **references** to other clusters (elements).
|
||||
|
||||

|
||||

|
||||
|
||||
There are two types of galaxies, the **regular** galaxy and the **matrix** galaxy.
|
||||
|
||||

|
||||

|
||||
|
||||

|
||||

|
||||
|
||||
|
||||
The difference between both is already clear when you add them in the MISP interface. In essence the matrix style galaxies allow you to select -multiple- values in a matrix-style like (obvious, right?), whereas the regular galaxy is a straightforward element from a list. You will most likely recognise these matrix types from the galaxies used to represent the [MITRE ATT&CK Framework](https://attack.mitre.org/)
|
||||
|
|
@ -230,7 +231,7 @@ What remains is linking the values to the correct matrix tab and matrix column.
|
|||
|
||||
This will put "Analysis of vulnerabilities and threats" in the column "CSIRT" in the tab "prior-to-incident-crime".
|
||||
|
||||

|
||||

|
||||
|
||||
## Automation, sort of ...
|
||||
|
||||
|
|
@ -260,6 +261,6 @@ sudo -u www-data /var/www/MISP/app/Console/cake Admin updateGalaxies force
|
|||
|
||||
The newly created matrix should then be visible under **Galaxies**, **List Galaxies**.
|
||||
|
||||

|
||||

|
||||
|
||||
If all looks good, you can do a pull request to make sure the next galaxy is available for the MISP community.
|
||||
|
|
@ -1,12 +1,13 @@
|
|||
---
|
||||
title: MISP service monitoring (and a bit of healing) with OpenNMS
|
||||
date: 2020-08-18
|
||||
layout: post
|
||||
authors:
|
||||
- Sascha Rommelfangen
|
||||
date: 2020-08-18
|
||||
tags: ["Monitoring", "OpenNMS", "MISP", "Threat Intelligence"]
|
||||
categories: []
|
||||
featured: /assets/images/opennms/sc-http-s-response_time.png
|
||||
banner: /img/blog/opennms/sc-http-s-response_time.png
|
||||
---
|
||||
|
||||
|
||||
|
|
@ -41,7 +42,7 @@ Assuming you have both a working MISP and an OpenNMS instance running, we can ju
|
|||
|
||||
This is the most simple form of monitoring in OpenNMS. It will be enabled by default and checks if the machine hosting MISP will be answering ICMP ('ping') packets. ICMP monitoring acts more like an on/off-switch monitoring, but it can also tell you statistically and historically something about the load of the machine and the network conditions due to the recorded response times.
|
||||
|
||||

|
||||

|
||||
|
||||
|
||||
### HTTP(S) monitoring
|
||||
|
|
@ -50,7 +51,7 @@ HTTP and HTTPS monitoring are also built-in into OpenNMS and activated by defaul
|
|||
|
||||
As in ICMP monitoring, OpenNMS is collecting the data over time and is able to give us an historic view on the response times without any additional configuration.
|
||||
|
||||

|
||||

|
||||
|
||||
|
||||
### Application monitoring
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.130 released (Various fixes, performance improvements and new features)
|
||||
date: 2020-08-21
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/d4_sshd_widget.png
|
||||
banner: /img/blog/d4_sshd_widget.png
|
||||
---
|
||||
|
||||
# MISP 2.4.130 released
|
||||
|
|
@ -1,12 +1,13 @@
|
|||
---
|
||||
title: MISP service monitoring with Cacti
|
||||
date: 2020-08-22
|
||||
layout: post
|
||||
authors:
|
||||
- Koen Van Impe
|
||||
date: 2020-08-22
|
||||
tags: ["Monitoring", "Cacti", "MISP", "Threat Intelligence"]
|
||||
categories: []
|
||||
featured: /assets/images/monitor-cacti/cacti-exp.jpg
|
||||
banner: /img/blog/monitor-cacti/cacti-exp.jpg
|
||||
---
|
||||
|
||||
|
||||
|
|
@ -61,11 +62,11 @@ And finally, add these Data Queries
|
|||
|
||||
Afterwards click on **Create Graphs for this Device** to get an overview of available graphs. Then select the desired graphs and click on **Create**.
|
||||
|
||||

|
||||

|
||||
|
||||
Allow it a bit of time so that Cacti can create the RRD files (RRDs are little 'databases' containing the statistics data) and poll sufficient information. If all goes well, you should have graphs similar to the ones below.
|
||||
|
||||

|
||||

|
||||
|
||||
|
||||
## MISP Workers and Statistics
|
||||
|
|
@ -140,7 +141,7 @@ To add the data source, click on **Data Source** under Templates, and then in th
|
|||
1. Set the **minimum** and **maximum** value to no minimum/no maximum with **U**
|
||||
1. Add the OID corresponding with the SNMP value, this is the OID you retrieved via the snmptranslate command in the previous step.
|
||||
|
||||

|
||||

|
||||
|
||||
You have to complete this step for all the data you'd like to be monitored, for example the job count, statistics, users, etc.
|
||||
|
||||
|
|
@ -154,7 +155,7 @@ Add the graph template via **Graph** under Templates, and then in the upper righ
|
|||
|
||||
You can leave all the other values to their default settings.
|
||||
|
||||

|
||||

|
||||
|
||||
You have to complete this step for all the data you'd like to be graphed, based on the previous created data sources.
|
||||
|
||||
|
|
@ -162,11 +163,11 @@ You have to complete this step for all the data you'd like to be graphed, based
|
|||
|
||||
The final step is to add this graph template to your monitoring device. Under Management, Devices choose the MISP device and scroll down to Associated Graph Templates. If all is good, the newly created Graph Template should be available under Add Graph Template. Select it and click Add.
|
||||
|
||||

|
||||

|
||||
|
||||
Then click **Create Graphs for this Device**, select the newly added graph and click Create.
|
||||
|
||||

|
||||

|
||||
|
||||
Similar as with the previous Cacti graphs, you need to give it some time before the values are collected and represented in the graphs.
|
||||
|
||||
|
|
@ -191,16 +192,16 @@ Add a new **Data Collector** under Data Collection. This new data collector will
|
|||
1. Point it to the script you just added.
|
||||
1. Add two output fields, which should point to the two fields returned by the script (time_connect and time_total).
|
||||
|
||||

|
||||

|
||||
|
||||
#### Graph Template and add to device
|
||||
|
||||
Now similar as for the graphing of MISP information, add a new graph template and include the HTTP response code data source. Afterwards add the graph template to your device, and create a new graph based on this template.
|
||||
|
||||

|
||||

|
||||
|
||||
## Dashboard
|
||||
|
||||
If all goes well, you should be able to build a dashboard in Cacti, representing the crucial MISP values.
|
||||
|
||||

|
||||

|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.131 released (improvements, bug fixes and major update to JavaScript dependencies)
|
||||
date: 2020-09-08
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/d4_sshd_widget.png
|
||||
banner: /img/blog/d4_sshd_widget.png
|
||||
---
|
||||
|
||||
# MISP 2.4.131 released
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: MISP 2.4.132 released (security fix CVE-2020-25766 and bugs fixed)
|
||||
date: 2020-09-21
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/d4_sshd_widget.png
|
||||
banner: /img/blog/d4_sshd_widget.png
|
||||
---
|
||||
|
||||
# MISP 2.4.132 released
|
||||
|
|
@ -1,12 +1,13 @@
|
|||
---
|
||||
title: Create an import script for MISP , step-by-step tutorial
|
||||
date: 2020-09-30
|
||||
layout: post
|
||||
authors:
|
||||
- Pauline Bourmeau
|
||||
date: 2020-09-30
|
||||
tags: ["MISP", "Import Script", "MISP", "Threat Intelligence"]
|
||||
categories: []
|
||||
featured: /assets/images/misp/blog/misp-python.png
|
||||
banner: /img/blog/misp-python.png
|
||||
---
|
||||
|
||||
# Create an import script for MISP in Python, step-by-step tutorial
|
||||
|
|
@ -1,7 +1,8 @@
|
|||
---
|
||||
title: Event Report - A convenient mechanism to edit, visualize and share reports
|
||||
date: 2020-10-08
|
||||
layout: post
|
||||
featured: /assets/images/misp/blog/event-reports/report-modal.png
|
||||
banner: /img/blog/event-reports/report-modal.png
|
||||
---
|
||||
|
||||
# Event Report: A convenient mechanism to edit, visualize and share reports
|
||||
|
|
@ -17,14 +18,14 @@ This article presents the most recently introduced feature to manipulate and sha
|
|||
|
||||
## New feature: *Event report*
|
||||
**Note**: In order to have a meaningful example, excerpts of the article from welivesecurity.com about [Winnti Group targeting universities in Hong Kong](https://www.welivesecurity.com/2020/01/31/winnti-group-targeting-universities-hong-kong/) have been encoded.
|
||||
The full demo *event* along with the *event report* is available [here](/assets/images/misp/blog/event-reports/misp.event-report-demo.json).
|
||||
The full demo *event* along with the *event report* is available [here](/img/blog/event-reports/misp.event-report-demo.json).
|
||||
|
||||
### Basic operations: Creation, deletion and synchronization
|
||||
As the name *Event report* indicates, reports in MISP are contained inside an *event*. It is important to note that *events* can contain more than one report.
|
||||
|
||||
*Event reports* can be revealed by clicking on the toggle button `Event reports` located in the event toolbar
|
||||
|
||||

|
||||

|
||||
|
||||
An *Event report* must have a name consisting of a few words summary about what you would expect in the report and a distribution level. The report's content can also be set here, but it is optional as a dedicated editor interface is available.
|
||||
|
||||
|
|
@ -36,16 +37,16 @@ To put it simply, *event reports* behave like attributes meaning that their dist
|
|||
A report's content can be non-formatted raw text but the power of the feature comes from its markdown parser.
|
||||
As a matter of fact, markdown format is **highly recommended** as it offers an easy-to-use syntax, a pleasant document, and if coupled with MISP custom directives, an easy-to-write pleasant interactive document!
|
||||
|
||||

|
||||

|
||||
|
||||
The editor interface presents a menu where reports can be downloaded in different formats and markdown rules can be turned on and off.
|
||||
Information on how to use the custom MISP markdown directives, supported markdown plugins and editor shortcuts can be found in the help menu.
|
||||
|
||||

|
||||

|
||||
|
||||
When it comes to editing, the best way to write a report is to use the split-screen mode as it offers both a text editor and a markdown viewer at the same time, providing an intuitive WYSIWYG experience.
|
||||
|
||||

|
||||

|
||||
|
||||
The editor provides features such as:
|
||||
- Markdown syntax shortcuts
|
||||
|
|
@ -73,22 +74,22 @@ Where **scope** represents the scope of the element being referenced and **UUID*
|
|||
Here are some examples with their UI appearance
|
||||
- **attribute:** `@[attribute](5f1accda-cde4-47fc-baf1-6ab8f331dc3b)`
|
||||
|
||||

|
||||

|
||||
- **object:** `@[object](e2293538-93a9-4c53-9c92-75ba75cfec3d)`
|
||||
|
||||

|
||||

|
||||
- **object's attribute:** `@[attribute](5f5907a9-7bcc-4676-9bd2-4f330a00020f)`
|
||||
|
||||

|
||||

|
||||
- **tag:** `@[tag](tlp:green)`
|
||||
|
||||

|
||||

|
||||
- **galaxy cluster:** `@[tag](misp-galaxy:malpedia="ShadowPad")`
|
||||
|
||||

|
||||

|
||||
- **galaxy matrix:** `@[galaxymatrix](c4e851fa-775f-11e7-8163-b774922098cd)`
|
||||
|
||||

|
||||

|
||||
|
||||
*Attributes* containing an attachment of a picture can also be displayed in the report with the following syntax
|
||||
```
|
||||
|
|
@ -101,7 +102,7 @@ Example:
|
|||
|
||||
With this special syntax, MISP elements can be referenced and reports become interactive by clicking on the rendered MISP elements.
|
||||
|
||||

|
||||

|
||||
|
||||
|
||||
### Editor autocompletion
|
||||
|
|
@ -109,11 +110,11 @@ The editor provides auto-completion for various types of datapoints. Once the `s
|
|||
|
||||
- Hinting with the filename value
|
||||
|
||||

|
||||

|
||||
|
||||
- Hinting with the threat actor tag
|
||||
|
||||

|
||||

|
||||
|
||||
## Summary
|
||||
With the support of reports built-in in MISP, a new kind of knowledge can be used. Classical threat intelligence reports, malware analysis articles or even something of a completely different taste can be shared along with the actionable data.
|
||||
Some files were not shown because too many files have changed in this diff Show More
Loading…
Reference in New Issue