|
|
||
|---|---|---|
| INSTALL | ||
| config | ||
| data/cache | ||
| db-bootstrap | ||
| public | ||
| scripts | ||
| .gitignore | ||
| .gitmodules | ||
| LICENSE.txt | ||
| README.md | ||
| behat.yml | ||
| build.properties | ||
| build.xml | ||
| composer.json | ||
| composer.phar | ||
| continuous.yml | ||
| init_autoloader.php | ||
| package.json | ||
| package.json.continuousphp | ||
| packages.json | ||
README.md
Skeleton Monarc Project
Disclaimer: This is a work in progress and software is still in alpha stage.
Introduction
CASES promotes information security through the use of behavioral, organizational and technical measures. Depending on its size and its security needs, organizations must react in the most appropriate manner. Adopting good practices, taking the necessary measures and adjusting them proportionally: all this is part of the process to ensure information security. Most of all, it depends on performing a risk analysis on a regular basis.
Although the profitability of the risk analysis approach is guaranteed, the investment represented by this approach in terms of the required cost and expertise is a barrier for many companies, especially SMEs.
To remedy this situation and allow all organizations, both large and small, to benefit from the advantages that a risk analysis offers, CASES has developed an optimised risk analysis method: MONARC (Method for an Optimised aNAlysis of Risks by CASES), allowing precise and repeatable risk management.
The advantage of MONARC lies in the capitalization of risk analyses already performed in similar business contexts: the same vulnerabilities regularly appear in many businesses, as they face the same threats and generate similar risks. Most companies have servers, printers, a fleet of smartphones, Wi-Fi antennas, etc. therefore the vulnerabilities and threats are the same. It is therefore sufficient to generalize risk scenarios for these assets (also called objects) by context and/or business.
More information: [Optimised risk analysis Method] (https://www.cases.lu/index-quick.php?dims_op=doc_file_download&docfile_md5id=56ee6ff569a40a5b52bed0e526a6a77f) (pdf)
Documentation
For installation guide see INSTALL.
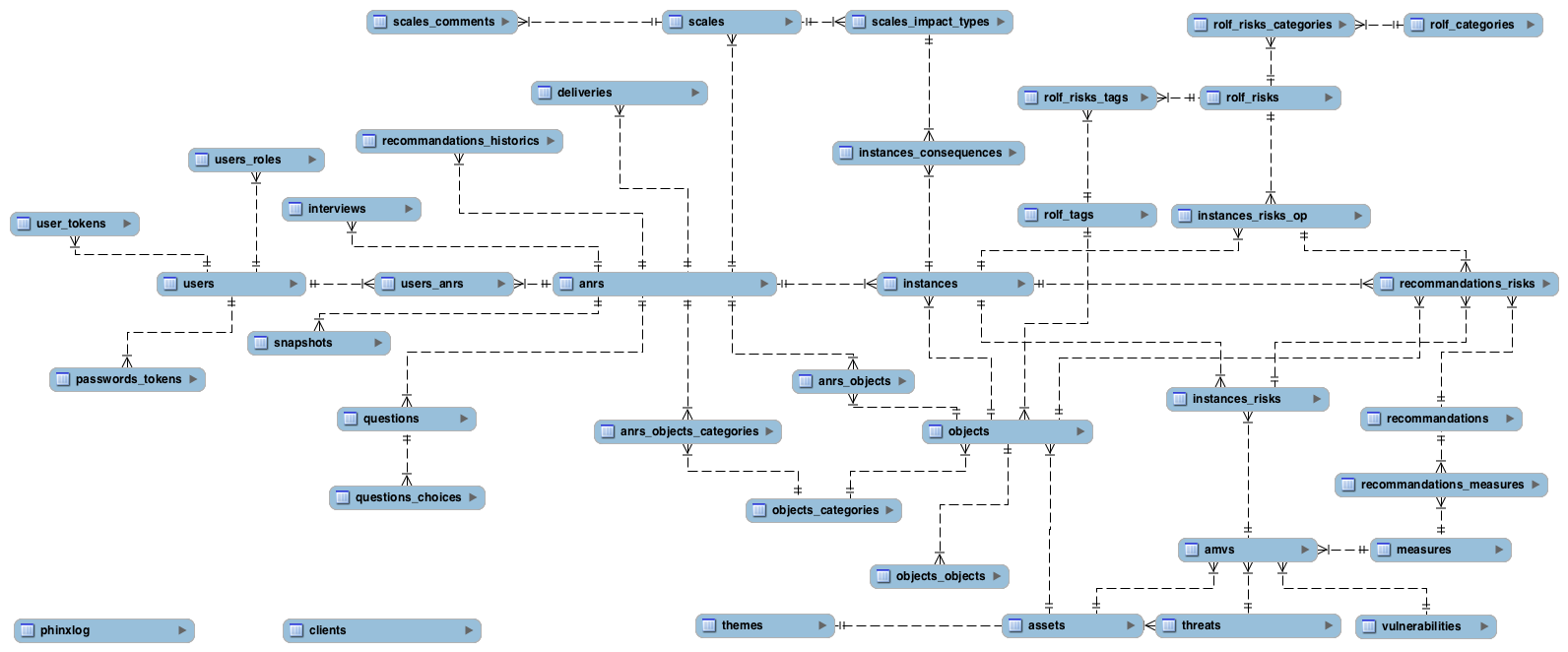
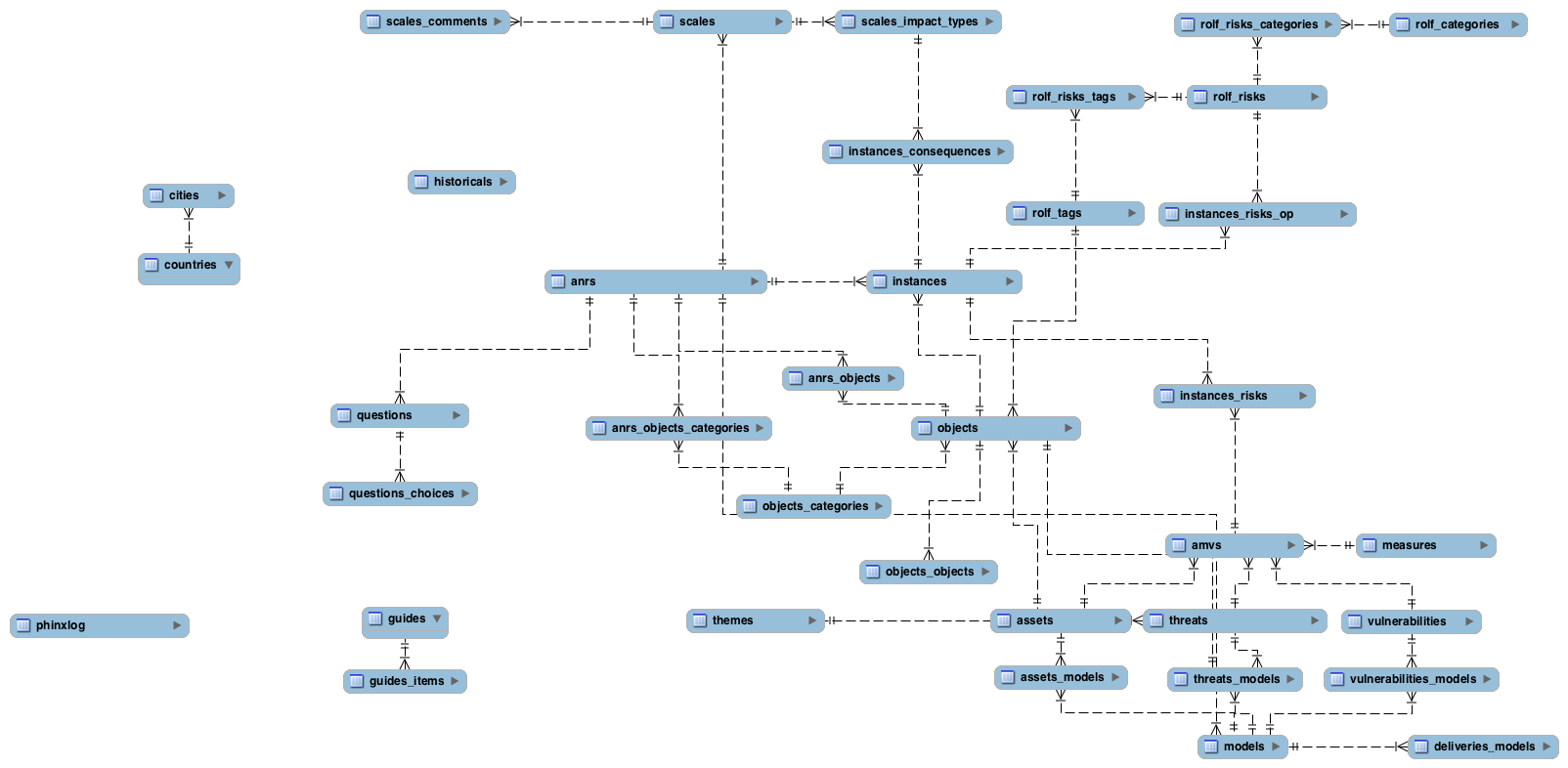
Data Model
License
This software is licensed under GNU Affero General Public License version 3
Copyright (C) 2016-2017 SMILE gie securitymadein.lu