|
|
||
|---|---|---|
| clusters | ||
| doc/images | ||
| galaxies | ||
| misp | ||
| tools | ||
| vocabularies | ||
| .travis.yml | ||
| CONTRIBUTE.md | ||
| LICENSE.md | ||
| README.md | ||
| jq_all_the_things.sh | ||
| schema_clusters.json | ||
| schema_galaxies.json | ||
| schema_misp.json | ||
| schema_vocabularies.json | ||
| validate_all.sh | ||
README.md
misp-galaxy
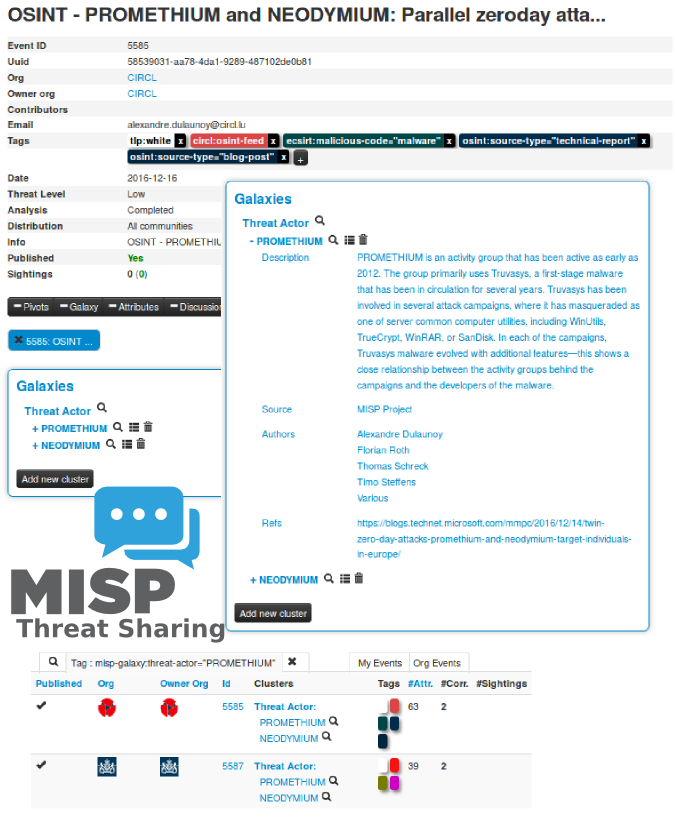
MISP galaxy is a simple method to express a large object called cluster that can be attached to MISP events or attributes. A cluster can be composed of one or more elements. Elements are expressed as key-values. There are default vocabularies available in MISP galaxy but those can be overwritten, replaced or updated as you wish.
Existing clusters and vocabularies can be used as-is or as a template. MISP distribution can be applied to each cluster to permit a limited or broader distribution scheme.
Vocabularies are from existing standards (like STIX, Veris, MISP and so on) or custom ones.
The objective is to have a comment set of clusters for organizations starting analysis but that can be expanded to localized information (which is not shared) or additional information (that can be shared).
Available clusters
-
clusters/android.json - Android malware galaxy based on multiple open sources.
-
clusters/banker.json - A list of banker malware.
-
clusters/stealer.json - A list of malware stealer.
-
clusters/backdoor.json - A list of backdoor malware.
-
clusters/botnet.json - A list of known botnets.
-
clusters/branded_vulnerability.json - List of known vulnerabilities and exploits.
-
clusters/exploit-kit.json - Exploit-Kit is an enumeration of some exploitation kits used by adversaries. The list includes document, browser and router exploit kits. It's not meant to be totally exhaustive but aim at covering the most seen in the past 5 years.
-
clusters/microsoft-activity-group.json - Activity groups as described by Microsoft.
-
clusters/preventive-measure.json - Preventive measures.
-
clusters/ransomware.json - Ransomware galaxy based on https://docs.google.com/spreadsheets/d/1TWS238xacAto-fLKh1n5uTsdijWdCEsGIM0Y0Hvmc5g/pubhtml
-
clusters/rat.json - remote administration tool or remote access tool (RAT), also called sometimes remote access trojan, is a piece of software or programming that allows a remote "operator" to control a system as if they have physical access to that system.
-
clusters/tds.json - TDS is a list of Traffic Direction System used by adversaries.
-
clusters/threat-actor.json - Adversary groups - Known or estimated adversary groups targeting organizations and employees. Adversary groups are regularly confused with their initial operation or campaign. MISP
-
clusters/tool.json - tool is an enumeration of tools used by adversaries. The list includes malware but also common software regularly used by the adversaries.
-
clusters/mitre-attack-pattern.json - Attack Pattern - MITRE Adversarial Tactics, Techniques & Common Knowledge (ATT&CK) - v1.0
-
clusters/mitre-course-of-action.json - Course of Action - MITRE Adversarial Tactics, Techniques & Common Knowledge (ATT&CK) - v1.0
-
clusters/mitre-intrusion-set.json - Intrusion Set - MITRE Adversarial Tactics, Techniques & Common Knowledge (ATT&CK) - v1.0
-
clusters/mitre-malware.json - Malware - MITRE Adversarial Tactics, Techniques & Common Knowledge (ATT&CK) - v1.0
-
clusters/mitre-tool.json - Tool - MITRE Adversarial Tactics, Techniques & Common Knowledge (ATT&CK) - v1.0
-
clusters/mitre-enterprise-attack-attack-pattern.json - Attack Pattern - MITRE Adversarial Tactics, Techniques & Common Knowledge (ATT&CK) - v2.0 Enterprise Attack
-
clusters/mitre-enterprise-attack-course-of-action.json - Course of Action - MITRE Adversarial Tactics, Techniques & Common Knowledge (ATT&CK) - v2.0 Enterprise Attack
-
clusters/mitre-enterprise-attack-intrusion-set.json - Intrusion Set - MITRE Adversarial Tactics, Techniques & Common Knowledge (ATT&CK) - v2.0 Enterprise Attack - Malware - MITRE Adversarial Tactics, Techniques & Common Knowledge (ATT&CK) - v2.0 Enterprise Attack
-
clusters/mitre-enterprise-attack-tool.json - Tool - MITRE Adversarial Tactics, Techniques & Common Knowledge (ATT&CK) - v2.0 Enterprise Attack
-
clusters/mitre-mobile-attack-attack-pattern.json - Attack Pattern - MITRE Adversarial Tactics, Techniques & Common Knowledge (ATT&CK) - v2.0 Mobile Attack
-
clusters/mitre-mobile-attack-course-of-action.json - Course of Action - MITRE Adversarial Tactics, Techniques & Common Knowledge (ATT&CK) - v2.0 Mobile Attack
-
clusters/mitre-mobile-attack-intrusion-set.json - Intrusion Set - MITRE Adversarial Tactics, Techniques & Common Knowledge (ATT&CK) - v2.0 Mobile Attack
-
clusters/mitre-mobile-attack-malware.json - Malware - MITRE Adversarial Tactics, Techniques & Common Knowledge (ATT&CK) - v2.0 Mobile Attack
-
clusters/mitre-mobile-attack-tool.json - Tool - MITRE Adversarial Tactics, Techniques & Common Knowledge (ATT&CK) - v2.0 Mobile Attack
-
clusters/mitre-pre-attack-attack-pattern.json - Attack Pattern - MITRE Adversarial Tactics, Techniques & Common Knowledge (ATT&CK) - v2.0 Pre Attack
-
clusters/mitre-pre-attack-intrusion-set.json - Intrusion Set - MITRE Adversarial Tactics, Techniques & Common Knowledge (ATT&CK) - v2.0 Pre Attack
-
clusters/sectors.json - Activity sectors
-
clusters/cert-eu-govsector.json - Cert EU GovSector
Available Vocabularies
A readable PDF overview of the MISP galaxy is available or HTML and generated from the JSON.
Common
- vocabularies/common/certainty-level.json - Certainty level of an associated element or cluster.
- vocabularies/common/threat-actor-type.json - threat actor type vocab as defined by Cert EU.
- vocabularies/common/ttp-category.json - ttp category vocab as defined by Cert EU.
- vocabularies/common/ttp-type.json - ttp type vocab as defined by Cert EU.
Threat Actor
- vocabularies/threat-actor/cert-eu-motive.json - Motive vocab as defined by Cert EU.
- vocabularies/threat-actor/intended-effect-vocabulary.json - The IntendedEffectVocab is the default STIX vocabulary for expressing the intended effect of a threat actor. STIX 1.2.1
- vocabularies/threat-actor/motivation-vocabulary.json - The MotivationVocab is the default STIX vocabulary for expressing the motivation of a threat actor. STIX 1.2.1
- vocabularies/threat-actor/planning-and-operational-support-vocabulary.json - The PlanningAndOperationalSupportVocab is the default STIX vocabulary for expressing the planning and operational support functions available to a threat actor.
- vocabularies/threat-actor/sophistication.json - The ThreatActorSophisticationVocab enumeration is used to define the default STIX vocabulary for expressing the subjective level of sophistication of a threat actor.
- vocabularies/threat-actor/type.json - The ThreatActorTypeVocab enumeration is used to define the default STIX vocabulary for expressing the subjective type of a threat actor.
MISP Integration
Starting from MISP 2.4.56, galaxy is integrated within the MISP threat sharing platform and users can directly benefit from the available clusters to attach them to the MISP event.
How to contribute?
License
The MISP galaxy (JSON files) are dual-licensed under:
- CC0 1.0 Universal (CC0 1.0) - Public Domain Dedication.
or
Copyright (c) 2015-2019 Alexandre Dulaunoy - a@foo.be
Copyright (c) 2015-2019 CIRCL - Computer Incident Response Center Luxembourg
Copyright (c) 2015-2019 Andras Iklody
Copyright (c) 2015-2019 Raphael Vinot
Copyright (c) 2015-2019 Deborah Servili
Copyright (c) 2016-2019 Various contributors to MISP Project
Redistribution and use in source and binary forms, with or without modification,
are permitted provided that the following conditions are met:
1. Redistributions of source code must retain the above copyright notice,
this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice,
this list of conditions and the following disclaimer in the documentation
and/or other materials provided with the distribution.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND
ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED.
IN NO EVENT SHALL THE COPYRIGHT HOLDER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT,
INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING,
BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE,
DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF
LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE
OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED
OF THE POSSIBILITY OF SUCH DAMAGE.